IoT Security is an important focus for enterprise leaders in the era of connected devices. Because it is overwhelming in industrial control systems, healthcare, and corporate environments. The advantage of connected and smart devices is that they are becoming the norm. Particularly, from smart sensors and smart meters to medical monitors. These devices purposefully help businesses, but they also come with an entirely different level of attack surfaces. Most designers have not designed IoT devices to be secure. They are vulnerable to breaches, botnets, and access by unauthorized access. The trend of digital transformation and the extended enterprise edge means securing IoT infrastructure is a given moving forward.
This guide describes what IoT Security is. Additionally, why is it different than traditional cybersecurity? And how to build a strategy to protect connected systems, data, and business operations at scale.
What Is IoT Security?
IoT Security encompasses the methods, technologies, and policies aimed at protecting Internet of Things (IoT) devices. Also, the networks their devices connect to, cyber threats. It includes securing the devices’ endpoints, data communications, and also the extensive infrastructure that enables connected ecosystems.
As companies deploy IoT to increase efficiencies, automation, and eventually intelligent operations. Security teams must defend against cyber threats on many devices. Further, these devices can use minimal power, are difficult to patch, and may be deployed in uncontrolled environments.
The U.S. National Institute of Standards and Technology (NIST) states that IoT Security is “the capability to secure, throughout the lifecycle of the device, the information and the functionality of the device and the networks that devices are connected to”. It supports lifecycle management of risk related to device data and behavior and its confidentiality, integrity, and availability.¹
The European Union Agency for Cybersecurity (ENISA) defines IoT Security as “the preservation of the availability, integrity, and confidentiality of the data and services in the presence of internal or external threats.” Lifecycle management is an essential factor for resiliency in connected systems.
IoT Security is ultimately a governance issue. So, in terms of enterprises, it entails including device visibility, identity management, threat detection, and compliance controls. All of this inside a sizeable security architecture to formulate one integrated security operation.
Why IoT Security Devices Are Hard to Secure
Although IoT devices are deemed valuable from the perspective of effective efficiency and real-time visibility. They are regarded as one of the toughest aspects of the enterprise infrastructure to secure, inherent in IoT devices. Unlike traditional IT systems, IoT endpoints were often designed with bare-bones security controls. This makes them inherently insecure and also difficult to manage at scale.
1. Limited Processing Power and Memory
A majority of IoT devices operate on lightweight hardware. This cannot run traditional security agents or even encryption algorithms. Eventually, it is making them an almost impossible candidate for traditional endpoint protections or intrusion prevention, or mechanisms for the secure boot process. In most cases, security takes a back seat to the low cost and also power-efficient designs.
2. Hardcoded Credentials and Insecure Default
An extraordinary amount of IoT devices are shipped with default passwords or hardcoded admin credentials, which simply aren’t likely ever changed after it is deployed. Eventually, these credentials are documented on the dark web. And as attackers are scanning the internet for vulnerable devices, these documented credentials provide a light and easy way onto the device.
3. Lack of Patchability and Longevity in IoT Security
No comparison, IoT devices are seldom, if ever, designed for updates. Most do not support secure over-the-air (OTA) mechanisms, meaning that vulnerabilities may exist for years after discovery. In industries like healthcare or manufacturing, some devices may be in use for as long as a decade, never updated.
4. Physical Exposure and Remote Deployment
IoT devices are deployed in unaudited or remote areas. factory floors, pipelines, onboard vehicles, public infrastructure, etc. It is making them easier to manage and also to tamper with physically. An attacker can almost effortlessly leverage any unsecured ports, flash malicious firmware on them, or intercept as they communicate with the rest of the device world.
5. Device Diversity and Vendor Fragmentation
Most enterprise networks contain multiple IoT devices from multiple vendors. So, each with its own proprietary protocols, firmware variants, and management interfaces. This diversity and fragmentation of devices increases the difficulty of standardizing security posture across an organization and often leads to blind spots in the network. Leading cybersecurity vendors such as Palo Alto Networks have emphasized how vulnerable IoT endpoints expand the attack surface, particularly in industries like healthcare and critical infrastructure.
6. Lack of Visibility in Traditional Security Tools
Many IoT devices exist beyond traditional IT asset management and endpoint detection tools. Sometimes, security teams cannot understand what devices are connected because they don’t have deep network visibility or behavioral analytics, which typically leads to not knowing what type of data is flowing through them or if they have been compromised.
The complexity of IoT security is unique because it encapsulates physical, cyber, and operational risks. Doing so in a manner that emphasizes evolving from legacy firewalls and antivirus platforms does not go far enough. new tactics such as continuous monitoring, segmentation, and identity-driven are required to achieve success.
Informative Components of an Organization’s IoT Security Strategy
Securing enterprise-wide IoT infrastructure is not just about locking down devices. The sentence focuses on creating a layered, integrated strategy of discovery, control, monitoring, and resilience. As enterprise IoT deployments continue to grow across supply chains, smart buildings, health care environments, and additionally industrial systems, CSOs need to adopt an architecture of IoT with a strong rationale that it is an extension of the organization’s security perimeter. Here are the key components of an effective enterprise IoT security strategy:
1. Asset Discovery & Visibility
The first rule of IoT is simple: you can’t protect what you can’t see. So, Organizations need to continuously scan for any device connected to the network across all environments – IT and OT – and keep an accurate asset inventory. Many of the newer asset discovery solutions use passive traffic analysis, deep packet inspection, and device fingerprinting to automatically discover unmanaged, rogue or un-trustworthy devices in real-time. So, in the future, make sure to integrate IoT discovery with your enterprise-wide SIEM or CMDB for a unified.
2. Network Segmentation
IoT devices should not exist on the same flat network as core business systems. Because, Network segmentation leveraging VLANs, SD-WAN, or software-defined perimeters can containerize breaches and reduce lateral movement. Further, micro-segmentation applies network policies more granularly down to individual device types or functions. And with IoT devices, we apply zero-trust principles by default. That is, avoiding trust in all communications with IoT until otherwise validated. Security platforms from HPE Aruba and Cisco offer built-in microsegmentation and traffic visibility features tailored for IoT-heavy networks.
3. Authentication and Identity Management
Each device must have its own verifiable identity. IoT security strategies must accept certificate-based authenticated devices using cryptographic device IDs. Eventually, along with be integrated with enterprise IAM or PKI systems. Avoid passwords and default credentials like the plague. In addition to mutual TLS (mTLS), hardware can also secure strong authentication through secure elements.
4. Secure Communication Protocols
Unencrypted device traffic is an open invitation to man-in-the-middle attacks. Enterprises must require the use of secure communication standards like TLS and HTTPS, and communication standards with secure messaging encryption like MQTT-S, CoAPs, or DTLS, depending on their use case. Enterprises must also check traffic logs for unencrypted usernames and/or passwords, or use of non-standard encrypted ports.
5. Firmware and Update Management
Outdated firmware and insecure update processes can cause vulnerabilities. Organizations should implement the expectation that IoT devices support cryptographically signed updates and will check for patches automatically or during a scheduled maintenance window. Include a firmware validation and also patch management plan in your risk policy. According to threat research from companies like Fortinet and Armis, insecure firmware and outdated operating systems are among the most exploited components in IoT environments.
6. Threat Detection and Anomalies
Regardless of how many checks and balances are put in place, traditional antivirus does not work for all IoT, but there is also behavioral analytics and network-based detection. AI-driven monitoring tools can use analytics to detect deviations in traffic flow, command behavior, and communications between devices when compromise occurs. Try coupling anomaly detection with threat intel feeds to identify known attack signatures and zero-day behavior.
7. Physical Security Controls
In some high-risk or remote environments, IoT devices must be physically secured from tampering. This may include safeguarding capsules, or providing tamper-proof labels or seals, and disabling unused ports, circuits, or interfaces. Physical access to IoT devices must be treated like another facet of your cyber posture, as with OT/ICS.
8. Vendor and Supply Chain Risk Management
A myriad of vulnerabilities in IoT stems from upstream suppliers, whether from insecure firmware, undocumented backdoors, or incomplete post-sale support. Enterprises should integrate security requirements into procurement contracts and require their vendors to supply software bill of materials (SBOMs). Assess your vendors against a NIST or ENISA IoT security baseline before deployment.
9. Lifecycle Management and Decommissioning
IoT devices, when retired from use, need to be decommissioned securely. This includes wiping down any stored information, revoking digital certificates or tokens, and also serious consideration towards removing any connection to the enterprise systems. Treating the IoT lifecycle management process like user off-boarding. Automating the process and periodically auditing it will make it a smaller task when it comes to data security.
An IoT security strategy will only provide you with true security if it is able to provide real-time visibility and also highly enforceable policy controls and lifecycle governance. It is not simply about bolting on protections to existing hardware or software; it is about building security into the architecture of your connected ecosystem.
Regulatory and Compliance Issues for IoT Security
The regulatory environment is rapidly evolving, with the use of IoT device deployments going into critical infrastructure, health care, and enterprise-level applications as part of a long-term digital transformation. Given this, CISOs need to understand that regulatory oversight is not only a reality for industries that have oversight authorities, but continuous compliance regulation developments, data protection acts, and industry standards will be among the considerations for their IoT strategy, not only to avoid levied fines but also to limit reputational harm and to ensure business continuity.
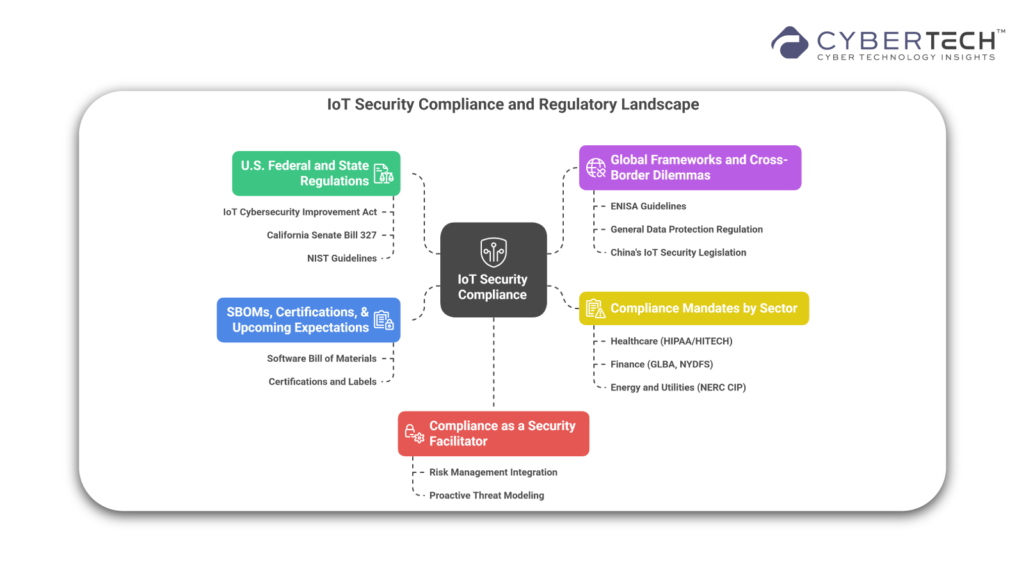
1. U.S. Federal and State Regulations
Research introduced in the last few years identifies several regulatory requirements that depict how enterprises and governments must consider IoT security functional requirements:
- IoT Cybersecurity Improvement Act (2020): A law that provides minimum security requirements for IoT devices purchased by the federal government. This act primarily impacts federal contractors, but it not only shapes their committees, but it also indirectly impacts how contractors are expected to implement good practices in this area of development, especially regarding secure development and patching best practices.
- California Senate Bill 327: This bill is often noted as the first state-level IoT bill that mandated manufacturers to use “reasonable security features,” like unique default passwords and methods of authentication.
- NIST Guidelines (NIST SP 800-213 and 8259 Series): Related to practically applying regulations within the enterprise context, the evolving NIST publications continue to serve as a baseline for bringing risk management to federal and enterprise IoT systems, while providing foundational security standards, securely managing device life cycles, visibility, and baseline security capabilities.
Consider mapping your IoT policies to NIST’s Cybersecurity Framework & IoT-specific guidelines to assist with standardizing your readiness for audits.
2. Global Frameworks and Cross-Border Dilemmas
Multinational organizations are facing even more complexity due to requirements related to data localization, privacy rules, and varying IoT standards:
- ENISA Guidelines (Europe): The European Union Agency for Cybersecurity (ENISA) has published a set of core requirements for Internet of Things (IoT) cybersecurity, focused on supply-chain trust, device lifecycle security, and secure defaults.
- General Data Protection Regulation (GDPR): If your IoT device collects or processes information about an individual in the EU, the organization must follow aspects of the GDPR, such as data minimization, consent, and breach notification.
- China’s IoT Security Legislation: China, in its Cybersecurity Legislation, has specific provisions associated with IoT device registration requests, issues of data sovereignty, and encryption requests, and is more regionally tailored for iots in the industrial sectors.
Adopt a “Global First” IoT governance model that considers regulatory obligations applicable to your deployment footprint.
3. Compliance Mandates by Sector
Some sectors deal with compliance mandates that intersect with IoT deployments.
- Healthcare (HIPAA/HITECH): For connected medical devices that interface with protected health information (PHI), security measures and standards set forth by HIPAA must be adhered to. Risk assessments are critical, as is appropriate data encryption.
- Finance (GLBA, NYDFS): IoT-enabled devices used for financial services (like enhanced ATMs and surveillance systems) may fall under a set of legislation such as the Gramm-Leach-Bliley Act or New York Department of Financial Services Cybersecurity Regulation.
- Energy and Utilities (NERC CIP): Industrial IoT devices used in critical infrastructure propagate a cyber threat and must comply with the North American Electric. Reliability Corporation Critical Infrastructure Protection (NERC CIP) standards or similar practices to mitigate cyber risk.
4. SBOMs, Certifications, & Upcoming Expectations
There is a growing trend in the regulatory and applicable industry space to have more transparency around the software component and respective risk exposure of the IoT technology:
- Software Bill of Materials (SBOM): Executive Order 14028 and others have advocated for the transparency of software components across the supply chain, particularly for IoT and embedded systems.
- Certifications and Labels: Some governments and alliances are developing certification programs to label IoT products as secure-by-design or secure premises (the Cyber Trust Mark in the USA or ETSI EN 303 645 in the EU).
To mitigate risk management, require suppliers to provide SBOMs and demonstrate compliance with IoT security certifications during the procurement process. Companies like Synopsys and Anchore are helping enterprises automate SBOM generation and secure their software supply chain in line with new U.S. federal requirements.
5. Compliance as a Security Facilitator, Not a Check Box of IoT Security
Although compliance frameworks can establish minimum organizational standards, enterprise leaders should not think of compliance as a checklist. True maturity in IoT security is based on embedding compliance into an organization’s wider risk management programs, eventually building security into products, and building a company culture of proactive threat modeling across all departments.
CISO’s Point of View is that treating compliance reviews as an outstanding opportunity to assess third-party risk. Additionally, enforce supply chain security, and judge your internal policies against international standards.
Conclusion: The Future of IoT Security
IoT Security is no longer a niche issue – it is now an essential pillar in any organization’s enterprise cybersecurity strategy. As millions of connected devices continue to expand the digital attack surface, organizations must pivot from their traditional reactive defenses to an architecture-centric lifecycle approach to securing IoT ecosystems. Whether the organization is in healthcare, manufacturing, finance, or critical infrastructure, the ability to detect, secure, and govern connected devices is now a direct link between business resilience, compliance, and customer trust.
Leaders in security will need to adopt a consistent focus on visibility, automation, and the enforcement of policies across all IoT endpoints. As regulations tighten and threat complexity evolves, the enterprises that succeed in IoT Security as a continuously evolving discipline, and not as a once-and-done activity.
FAQs
1. Which steps do I take to formulate an IoT Security strategy?
The first step is to identify all connected devices, implement access controls, and segment your network. Then form policies regarding monitoring, updating devices, and risk mitigation.
2. Do existing cybersecurity tools apply to IoT Security devices?
Not always. The vast majority of IoT devices require tools that are specific to IoT, as they are too resource-constrained to run legacy security software.
3. Who is responsible for managing IoT Security in my organization?
IT Security and IT-related teams should own IoT Security, but it is a multi-dimensional evaluation involving obligations from the operations, compliance, and procurement teams.
4. How do I validate that an IoT product is secure?
You could ask the provider for security certifications, check their policies for updates, and validate that the device has support for encryption and remote administration control.
5. What if I find an unidentified or vulnerable IoT device?
Unplug it from the network, try to understand what it is used for, update the device if possible, and restrict its access to your network as best as possible until you can secure it.








