In the world of cybersecurity, it’s often the seemingly small breaches that lead to the biggest headaches. And in the case of AppLite, a new variant of the AntiDot banking trojan, the consequences can be devastating—not just for individuals, but for entire organizations. This sophisticated mobile-targeted phishing campaign has been specifically designed to target Android devices, stealing everything from banking credentials to corporate access, and it’s making waves across the cybersecurity landscape.
Recommended: CyberTech Top Voice: Interview with Zimperium’s Krishna Vishnubhotla
Meet Alex: The Victim Behind the Attack
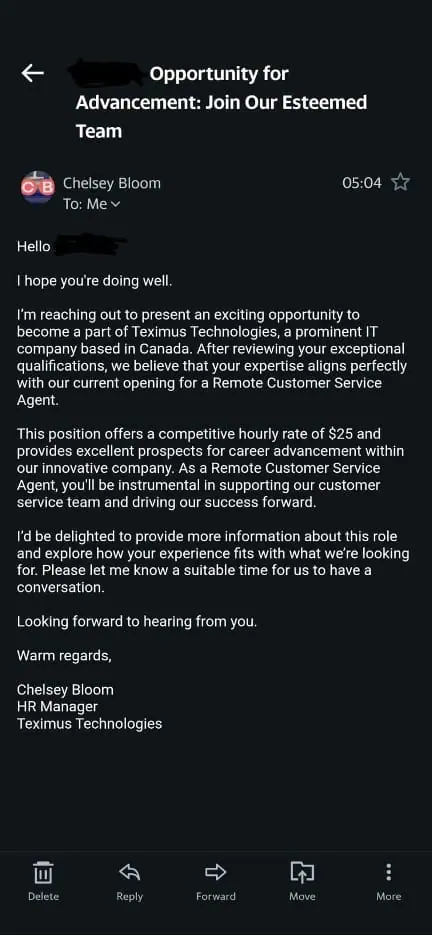
Let’s take a moment to understand just how devastating this attack can be through the eyes of someone who experienced it. Meet Alex, a mid-level employee at a growing tech company. Like many of us, Alex uses a smartphone for just about everything—personal emails, social media, and yes, work-related apps too. He’d recently applied for a job at a new company, and one morning, he received what seemed like a legitimate email from a recruiter. It looked professional, complete with a job offer and a link to apply further.
Curious, Alex clicked the link and, after answering a few questions, was asked to download an app to “continue the process.” Without thinking twice, he did. After all, the email seemed so real, and it was from a company he was genuinely excited to work for. What Alex didn’t know was that the app wasn’t just any application—it was a dropper for the AppLite trojan, which began its malicious work the moment it was installed.
Fast-forward a few days, and Alex noticed some odd behavior on his phone. Apps were crashing, new icons appeared, and his phone was running slower than usual. It wasn’t until he checked his bank account and noticed unauthorized transactions that the full extent of the breach became clear. The malware not only stole his personal banking credentials but, because Alex also used his phone for work emails and enterprise apps, it had access to corporate data. The worst part? The attackers could have accessed confidential company information had he been working remotely at the time.
This wasn’t just about Alex’s personal data—it was about the potential impact on the security of his entire organization.
What is AppLite Banker?
AppLite Banker, the latest variant of the AntiDot trojan, builds on an earlier version discovered by Cyble earlier in 2024. This strain is highly sophisticated and primarily targets Android devices through Mishing—a mobile-targeted phishing technique that convinces users to download malicious apps.
What makes AppLite particularly dangerous is its broad range of targets. While it’s often associated with stealing banking credentials, it also has access to other critical applications, including cryptocurrency wallets and corporate tools used for remote work.
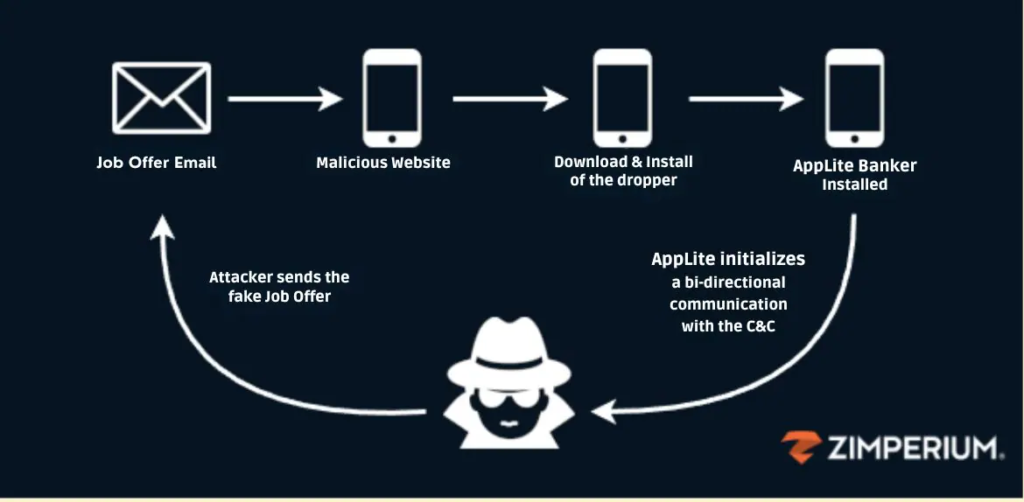
Cybersecurity researchers have uncovered a highly sophisticated mobile phishing (or mishing) campaign that delivers an updated version of the Antidot banking trojan. According to Zimperium zLabs researcher Vishnu Pratapagiri, the AppLite Trojan attackers pose as recruiters, luring victims with fraudulent job offers.
Latest CyberTech News: ProofID Strengthens SailPoint Partnership with Global MSP Status
As part of their scam, the phishing campaign tricks victims into downloading a malicious app that serves as a dropper, which eventually installs the updated Antidot trojan—now identified as AppLite Banker—on the victim’s device. This new variant, primarily targeting Android devices, can steal sensitive data like unlocking PINs, passwords, or patterns and even take remote control of the infected device. These capabilities, including device takeover, are reminiscent of the features recently seen in the TrickMo malware family.
Once installed, AppLite takes over the victim’s device and can:
- Steal sensitive credentials: This includes banking, cryptocurrency, and corporate login details.
- Gain access to enterprise applications: If the device is used for work purposes, attackers can access internal apps, company data, and confidential systems.
- Control the device: The malware gives attackers full control of the device, from camera and microphone access to stealing stored information.
How Does AppLite Spread?
Cybercriminals are increasingly exploiting the trust that employees place in their mobile devices. According to zLabs researchers, 76% of phishing sites targeting enterprises now use HTTPS, making the malicious sites appear legitimate to victims. Due to the smaller screens and less prominent security indicators on mobile devices—such as hidden URL bars—employees are less likely to recognize these phishing attempts, leaving them more vulnerable to attacks like AppLite.
The attackers behind this campaign have refined their methods, making it harder than ever to spot the threat. They use highly convincing social engineering tactics, posing as job recruiters or HR representatives from well-known companies. The phishing emails often look legitimate, complete with professional language and logos, which makes it easier for even tech-savvy individuals to fall for the scam.
For example, Alex received a fraudulent job offer from what appeared to be a reputable company. The email contained a link that led him to a fake job application portal, where he was tricked into downloading an app that acted as the malware’s dropper. Once downloaded, the dropper installed the AppLite trojan and began silently harvesting his credentials.
These attackers are adaptive and sophisticated. They know how to build trust, which makes their attacks so successful.
Why This Matters for CIOs and CISOs
The AppLite trojan isn’t just a threat to individuals like Alex—it’s a serious concern for entire organizations. As the lines between personal and work devices continue to blur, particularly with the rise of remote work and Bring Your Own Device (BYOD) policies, the risk of such attacks is growing. Employees like Alex are using their mobile devices for everything—personal tasks, social media, and, increasingly, work-related activities.
Here’s why AppLite should be on the radar for every CIO and CISO:
- It Targets Remote Workers: With more employees working remotely, many use personal mobile devices for business tasks—checking work emails, accessing enterprise applications, or even using messaging tools for communication. AppLite exploits this shift, making it easier for attackers to infiltrate corporate networks.
- Wide Access to Sensitive Data: Unlike traditional banking trojans, AppLite doesn’t just target banking apps—it’s capable of accessing corporate credentials, internal systems, and even private communications. If an employee like Alex uses their phone for work purposes, a breach like this could easily lead to a much larger compromise.
- Social Engineering is the Weak Link: The success of AppLite hinges on social engineering—convincing victims to download a malicious app. Phishing emails masquerading as job offers, HR communications, or business-related messages can bypass traditional security filters, making it harder for employees to detect.
- The Spread is Fast and Silent: Once installed, AppLite is designed to work in the background, without the victim’s knowledge. It quietly steals credentials, takes over the device, and opens the door for further exploitation. This makes it even harder for employees to spot until the damage is done.
How Can You Protect Your Organization?
Given the rising threat of AppLite and similar malware, here’s what you, as a CIO or CISO, can do to protect your organization:
- Educate Employees About Phishing: Awareness is key. Ensure that your employees know the dangers of phishing, how to spot suspicious emails, and the importance of verifying links before clicking. Simulated phishing exercises can help train employees to recognize real threats.
- Enforce Mobile Device Management (MDM): Using MDM solutions ensures that all mobile devices accessing corporate resources are compliant with your organization’s security policies. This includes enforcing app whitelisting and blocking unauthorized apps that could be used to deliver malware.
- Implement Multi-Factor Authentication (MFA): MFA is one of the best ways to protect sensitive corporate data. Even if an attacker steals an employee’s credentials, MFA can prevent them from accessing enterprise applications.
- Monitor and Respond Quickly: Implement real-time monitoring and alert systems that can detect suspicious activity across all devices. By spotting abnormal behavior early, you can prevent further damage.
- Vet Apps Before Downloading: Encourage employees to only download apps from trusted sources, like the official Google Play Store. Apps from third-party stores are much more likely to be infected with malware.
Zimperium vs. AppLite: Defending Against Mobile Threats
As mobile threats like the AppLite trojan grow increasingly sophisticated, security teams need to stay vigilant. The AppLite trojan, which targets Android devices, can steal sensitive data and compromise enterprise systems. Zimperium’s detection engine offers an effective solution by providing zero-day protection through real-time detection of malware and phishing attacks directly on the device.
Zimperium’s technology uses advanced machine learning and behavioral analysis to detect and mitigate threats without impacting device performance or app functionality. This type of on-device detection is crucial in defending against evolving threats like AppLite, which has extensive control over compromised devices. For mobile security teams, adopting proactive protection measures is key to safeguarding user data and preventing financial or operational damage from emerging malware.
Given the challenges posed by mobile threats, how are you currently managing mobile security for your team or organization?
Have you implemented any specific defense solutions against these advanced mobile threats?
Conclusion: The Growing Mobile Threat
AppLite is a stark reminder of how quickly mobile security threats can escalate. It’s not just about banking data anymore; it’s about corporate access, intellectual property, and even client confidentiality. For CIOs and CISOs, the lesson is clear: The security of mobile devices is more critical than ever, especially as remote work continues to grow. The best defense? A combination of employee education, robust mobile security protocols, and real-time monitoring to stay ahead of threats like AppLite.
In a world where attackers are using increasingly sophisticated methods, ensuring your team’s mobile security is no longer optional—it’s a necessity.
Source:
Pratapagiri, V. (2024) ‘AppLite: A new AntiDot variant targeting mobile employee devices’, Zimperium, 9 December.








