For most organizations, the inbox has quietly become the most exposed surface in the enterprise.
Not because teams lack tools. Not because awareness programs don’t exist. But, because the way email risk manifests today no longer matches how most security strategies are designed.
Cyberattacks increasingly begin with nothing more than a message that looks normal, arrives at the right moment, and asks for something reasonable. No malware. No red flags. No technical exploit. Just persuasion.
For security leaders, this shift changes everything.
What are Email Threats?
Email threats refer to adversarial techniques that use email as an entry point into organizations, combining social engineering, configuration weaknesses, and gaps in security controls to gain access. These attacks rely on deceptive messaging, varied delivery methods, and evasion strategies that allow them to slip past traditional defenses—making continuous validation and proactive assessment of email security posture essential.
Common Email Threats and Their Cost Impact on the Industry
Email-based attacks continue to drive some of the most financially damaging cybersecurity incidents across industries. The most prevalent threats include:
- Phishing and Credential Theft
Deceptive emails designed to harvest login credentials remain the most common attack type. Stolen credentials are frequently reused to access cloud services, internal systems, and third-party platforms, leading to account takeovers, data exposure, and downstream attacks. The financial impact often includes incident response costs, identity remediation, and prolonged business disruption. - Business Email Compromise (BEC)
BEC attacks exploit trust and authority to trigger fraudulent payments or data disclosure. These incidents are among the costliest email-driven threats, frequently resulting in direct financial losses, legal exposure, and recovery efforts that can span months. Because BEC attacks often lack malware, they are also harder to detect and investigate. - Malicious Attachments and Payload Delivery
Weaponized files—such as executables or HTML-based lures—are used to deploy ransomware, remote access tools, or information stealers. The resulting impact can include system downtime, ransom payments, regulatory penalties, and long-term operational recovery costs. - Malicious Links and Cloud-Based Phishing
Emails containing links to fake authentication portals or compromised cloud resources drive credential theft and lateral movement. These attacks contribute to broader breach events, increasing the total cost through extended dwell time and expanded scope of compromise. - Supply-Chain and Vendor Impersonation Attacks
By impersonating trusted partners or infiltrating third-party accounts, attackers introduce fraud and malware through legitimate-looking communications. These incidents often affect multiple organizations simultaneously, amplifying financial impact across ecosystems.
What Industry Research Says About Email Threats
Collectively, email threats account for billions in global losses each year, driven by direct fraud, ransomware incidents, business interruption, regulatory fines, and reputational damage. Beyond immediate financial harm, organizations also face increased cyber insurance premiums, audit scrutiny, and long-term erosion of customer and partner trust.
For many enterprises, email is no longer just a communication channel—it is a primary driver of cyber risk exposure and cost. Industry research increasingly supports this shift.
According to Barracuda’s Email Threat Report 2025,” email continues to be the primary entry point for cyber intrusions, serving as a delivery channel for weaponized files, deceptive links, and social engineering tactics designed to compromise systems and users.
Another cybersecurity leader, Darktrace, pointed out that the increasing accessibility of generative AI has further elevated BEC risk.
What is BEC? It stands for Business Email Compromise.
Even with native cloud protections and secure email gateways in place, Darktrace found that approximately 17% of high-risk emails evade detection during initial screening. These gaps are particularly significant for BEC risks, where messages often lack malware or links and therefore bypass controls designed to catch technical indicators rather than deceptive intent.
Advanced language models enable adversaries to produce highly credible messages, automate personalization, and scale deception efforts. In practice, this often manifests as realistic vendor correspondence—such as falsified invoices tied to ongoing projects—that closely mirrors authentic business communications.
According to Sophos’ 2025 State of Ransomware, email remains a dominant ransomware delivery mechanism, with 37% of victims attributing their breach to either malicious email or phishing, up from 11% phishing-related incidents reported the year before.
Email Risk Has Moved From Infrastructure to Influence
Email threats used to be mechanical. Malicious files. Suspicious domains. Known indicators that could be blocked at scale.
That era is ending.
Today’s attacks are built around timing, credibility, and social context. Messages arrive from real accounts. They reference real conversations. They exploit business pressure rather than technical gaps.
What’s changed is not the channel—it’s the intent model.
Attackers no longer need to defeat systems. They aim to convince people.
Why Modern Attacks Evade Traditional Controls
While socially engineered emails increasingly arrive without obvious payloads, attachments remain a high-risk vector when they do appear. Recent threat analysis shows that executable files carry the highest danger, with the vast majority of detected binaries containing malicious code capable of installing malware immediately upon launch.
HTML attachments, though sent far less frequently, also present outsized risk. Nearly one in four HTML files delivered via email are weaponized, commonly redirecting recipients to fraudulent login pages or harvesting credentials under the guise of legitimate content.
These patterns reinforce a critical reality for security leaders: attachment risk is defined by intent and file behavior—not volume. Low-frequency formats can still represent disproportionate exposure if left unchecked.
Security programs still rely heavily on tools designed to intercept artifacts—files, links, domains, and IPs. But many of today’s most damaging incidents involve none of these.
Instead, they feature:
- Legitimate senders whose accounts were quietly taken over
- Requests that appear routine but are strategically timed
- Messages crafted to align with internal workflows and authority structures
- Cloud-hosted pages that change faster than detection engines can track
In these cases, conventional defenses often see nothing wrong—because technically, nothing is.
This is where many security leaders are realizing an uncomfortable truth: email security cannot be solved by detection alone.
The Real Blind Spot: Context
What’s missing from many email security architectures is contextual awareness.
Security systems typically don’t understand:
- How a specific executive normally communicates
- Whether a financial request fits historical behavior
- If a vendor message deviates from established patterns
- When urgency is being artificially manufactured
Without context, defenses become reactive. With context, they become predictive.
This distinction is now central to protecting modern enterprises.
From Blocking Threats to Interpreting Behavior
Forward-looking organizations are shifting their mindset. Instead of asking, “Is this message malicious?” they are asking, “Does this interaction make sense?”
That change unlocks a different level of protection.
By examining communication patterns, relationship history, and behavioral signals, security teams can identify high-risk emails even when no technical indicators exist.
This shift positions email security as a safeguard for business decisions—not merely a mechanism for blocking threats.
Why Cloud Email Demands a New Security Model
As enterprises standardize on cloud email platforms, traditional perimeter concepts dissolve.
There is no gateway in the classic sense. There is no clean separation between internal and external. Trust is fluid—and attackers exploit that fluidity.
In this environment, effective protection depends on:
- Continuous analysis rather than point-in-time scanning
- Risk scoring instead of binary allow/deny decisions
- Adaptive models that evolve with organizational behavior
Security that doesn’t learn will always lag.
The Human Element Is Not the Weakest Link—It’s the Target
Security awareness often frames people as the problem. In reality, people are the objective.
Darktrace analysis shows that SEGs most frequently miss context-driven, low-signal attacks.
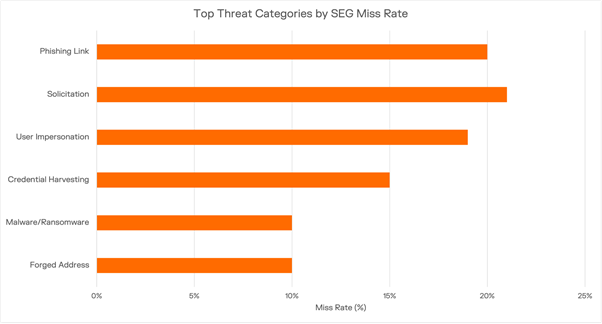
Attackers design messages to align with incentives, deadlines, and authority—not ignorance. The most successful compromises occur when capable professionals are placed under realistic pressure.
That’s why reducing email risk requires more than training completion metrics. It requires:
- Reinforcing decision-making under pressure
- Aligning security controls with real business workflows
- Treating employees as participants in defense, not liabilities
Resilience is built when technology and human behavior reinforce each other.
What Security Leaders Should Reconsider Now
For CISOs and CIOs, the challenge is no longer about adding another control—it’s about changing the mental model.
Email security must:
- Interpret behavior with contextual scanning of content
- Adapt continuously around static and dynamic enterprise email IT rules
- Protect decisions with policy-driven systems
- Reflect on how people actually work
The inbox is no longer a communication tool alone. It is a control plane for trust, authority, and access.
Organizations that adapt to this shift materially lower risk, while those that fail to do so remain trapped in a cycle of reacting to incidents that were never identified as threats.
CyberTech Insights explores how cybersecurity leadership is evolving as threat models change—not when breaches make headlines, but before they happen.
Because modern defense starts with understanding intent, not indicators.
FAQs
1. Why is email still the primary attack vector for enterprises?
Email remains central to business operations and decision-making, making it a high-value target. Attackers exploit trust, urgency, and familiarity—often without using malware—allowing malicious messages to blend into normal business communication.
2. What makes modern email threats harder to detect than traditional attacks?
Many current attacks rely on social engineering rather than technical exploits. Messages may originate from legitimate or compromised accounts and contain no links or attachments, making them difficult for rule-based or signature-driven defenses to identify.
3. How does Business Email Compromise differ from traditional phishing?
BEC attacks focus on manipulation rather than mass deception. They are typically targeted, highly contextual, and designed to trigger specific actions such as financial transfers or data disclosure, often bypassing controls that look for known indicators of compromise.
4. Why are native cloud email protections and secure email gateways no longer sufficient on their own?
While foundational, these tools are optimized for known threats and static patterns. They often lack the contextual and behavioral awareness needed to detect intent-based attacks that closely mimic legitimate business communication.
5. What should CISOs and CIOs prioritize to reduce email-driven risk in 2026?
Security leaders should focus on strategies that incorporate behavioral analysis, continuous assessment, and alignment with real business workflows—while reinforcing decision-making awareness among employees who are most frequently targeted.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at info@intentamplify.com.







