As Quantum Computing gets closer to real-world reality, cybersecurity executives face an emerging worry. that encryption that works today could fall short in the Quantum Cryptography breakthroughs of tomorrow. Algorithms such as RSA and ECC, which currently secure most digital systems, are becoming more susceptible to future attacks by quantum computers.
Quantum cryptography provides an entirely new approach, one that not only makes encryption more secure but also theoretically unbreakable, due to the laws of physics. To CISOs, CIOs, and security professionals, grasping this change is no longer a choice. It’s critical to long-term risk management and digital trust.
This article dives into what quantum cryptography is, how it works, and why it’s more important now than ever to the future of enterprise cybersecurity.
Defining Quantum Cryptography
Quantum cryptography is a security technique that applies the principles of quantum mechanics for defending information. As opposed to conventional cryptography, which is based on difficult mathematical problems to defend data, quantum cryptography applies the properties of subatomic particles to generate encryption keys that cannot be copied, foreseen, or secretly tapped.
Gartner defines it as,
“Quantum cryptography, and specifically quantum key distribution (QKD), employs quantum physics to securely exchange encryption keys. It can detect eavesdropping in real-time, which makes interception virtually impossible without the parties being notified.”
As stated by IBM:
“Quantum cryptography applies quantum mechanical properties to carry out cryptographic operations. It is not a matter of encrypting messages with quantum algorithms, but of allowing two parties to generate a shared random secret key that is only known to them, and that can then be used to encrypt and decrypt messages.”
(Source: IBM Quantum Research)
The most widely recognized use of quantum cryptography is Quantum Key Distribution (QKD). Indeed, QKD enables two parties to securely share a secret encryption key with complete assurance that no one else, a third party, has tapped and modified it. Quantum properties of photons, the smallest particles of light, make this possible. Researchers measure photons in unpredictable ways.
If an attacker attempts to intercept the quantum key, the measurement will cause the system to fluctuate and warn both receiver and sender of a threat. This is what is unique to QKD: it offers built-in intrusion detection at the physics level, rather than at the software or network level.
Short answer: Quantum cryptography not only encrypts your message but ensures that no one else can even see the key without detection.
How Does Quantum Cryptography Key Distribution Work?
The Role of Photons in Key Transmission
At the heart of QKD is the employment of photons, tiny packets of light, to transmit encryption key data. They imprint the photons with varying quantum states, e.g., polarization orientations. Since quantum particles are unstable when measured, any measurement or interception causes the photons to alter their state. This renders detection of interception impossible.
If a third party, that is an attacker, tries to intercept the quantum key, the system detects this interference immediately. This is a fundamental difference from traditional key exchanges, which observers can passively use without leaving a trace. In QKD, the sender and receiver will know the key has been compromised and can discard it, ensuring no false trust in a secure channel.
BB84: The First Quantum Key Protocol
One of the most extensively used QKD protocols is BB84. Charles Bennett and Gilles Brassard established this in 1984. It encodes data using two different sets of polarizations of the photons, horizontal/vertical and diagonal. The randomness and uncertainty of quantum states in BB84 are the foundations of secure key exchange.
Integration with Classical Encryption
Once they have shared a secure quantum key, the two can use it to encrypt and decrypt messages with classical symmetric encryption algorithms such as AES. The difference is that they exchanged the key in a provably secure fashion, even against future quantum computers.
Current Use and Deployment Models
QKD is already in the process of testing and deployment over optical fiber cables, satellite connections, and metropolitan quantum networks. European, Chinese, Japanese, and U.S. projects are looking into national-scale QKD infrastructure. Though still costly and distance-limited, these initiatives signal the dawn of a quantum-secure era.
Why Quantum Cryptography Is Relevant Today
- Classic encryption is vulnerable: Algorithms such as RSA and ECC will be obsolete when large-scale quantum computers are in use.
- Quantum computers are progressing fast: Companies like IBM and Google are advancing toward systems capable of breaking current encryption within the next decade.
- Data can be stolen today and decrypted later: Threat actors may already be harvesting encrypted data to decrypt once quantum capabilities emerge.
- Quantum cryptography offers physics-based protection: Unlike algorithmic methods, QKD ensures security through the laws of quantum mechanics, not computation.
- NIST and governments are preparing now: The U.S. and others are building post-quantum standards and making quantum-secure networks an investment.
- High-risk industries can’t wait.: Government, defense, finance, and healthcare lead the way due to extended data retention cycles and greater exposure.
Use Cases of Quantum Cryptography in Enterprise and Critical Infrastructure
Although quantum cryptography is in its infancy, various industries are already investigating the potential for practical applications. High priority is being placed upon safeguarding long-lifespan, high-value data that might be vulnerable once quantum computers are up and running.
1. Financial Institutions: Securing Interbank Transactions
Banks process large volumes of confidential information each second, from real-time payments to risk modeling and customer verification. Current encryption secures these flows today, but future quantum-based attacks have the potential to uncover past transactions if keys are harvested and subsequently decrypted.
Certain banks are currently pilot-testing quantum key distribution (QKD) to encrypt internal data transfer and interbank communications. The aim is to make sure that encryption keys cannot be tapped quietly, providing long-term data integrity, even as quantum computing comes of age. In an industry where trust is paramount, quantum cryptography offers future-proof protection for a post-quantum world.
2. Telecom Operators: Creating Quantum-Ready Networks
Telecom providers serve as the data transmission backbone for the globe and, therefore, are a central focus in the transition to quantum-resistant infrastructure. A number of the major players are testing QKD over current fiber networks to secure core network traffic and customer information in transit.
By integrating QKD into their networks, these operators are laying the groundwork for a day when quantum attacks become a reality, not just safeguarding their own networks, but also allowing secure services for customers in finance, healthcare, and government.
3. Government and Defense: National-Scale Data Protection
Quantum cryptography is a national security asset. Defense organizations and intelligence agencies handle secret information that can remain sensitive for decades. In contrast to conventional encryption, which can be broken over time, QKD provides tamper-evident key distribution that is immune to future technological breakthroughs.
China, the U.S., and also members of the EU are among the countries investing in national quantum networks and satellite-based QKD systems to provide secure military and diplomatic communications. These deployments demonstrate the tremendous priority governments put on being ahead of quantum-era cyber threats.
Benefits and Limitations of Quantum Cryptography
Quantum cryptography isn’t a silver bullet, but it presents a fundamentally new mechanism to protect data that is quantum-resistant and secure from future quantum attacks. That is what it has to offer and where the risks are.
Key Benefits
1. Physics-Based Security
Quantum cryptography, specifically Quantum Key Distribution (QKD), takes advantage of the principles of quantum mechanics rather than mathematical difficulty to provide data security. When a key is intercepted en route, it destroys the quantum state, revealing the attempt immediately.
2. Tamper Detection by Design
In traditional cryptography, data can be tapped in without any indication. With QKD, attempted eavesdropping is instantly visible, ensuring that it is impossible to intercept keys surreptitiously.
3. Long-Term Confidentiality
Quantum cryptography is especially valuable in safeguarding information with lengthy confidentiality lifecycles like national security files, financial agreements, or intellectual property that need to stay protected for decades.
4. Strategic Preparedness
Organizations can incorporate quantum preparedness into their security stance by adopting it early. Industry sectors such as finance, government, and telecom are piloting QKD today to prevent hasty migration in the future.
Limitations and Challenges
1. Infrastructure Dependency
QKD necessitates specialized equipment, such as photon transmitters, detectors, and special fiber lines. This complicates scaling over software-based encryption tools.
2. Distance Limitations
Present QKD systems function optimally over comparatively short distances (less than 100–200 km on fiber) without signal degradation. Satellite-based QKD extends this distance, but it remains experimental.
3. Expensive and Complex
It is costly to deploy QKD networks. Hardware, operating overhead, and interfacing with legacy systems are actual-world adoption barriers for companies not yet prepared to invest in the long term.
4. Not a Complete Replacement Yet
Quantum cryptography protects key exchange, but it will not encrypt the message data itself. It needs to be utilized together with classical encryption methods and doesn’t currently mitigate all forms of cyber threats.
Enterprise Adoption & Market Perspective
Governments and organizations worldwide are taking more and more action on the quantum threat. Further, the trend towards quantum-safe cryptography and QKD demonstrates a strategic turning point in business cybersecurity planning.
1. Early Widespread Adoption Trends
A poll conducted by the Capgemini Research Institute of 1,000 enterprises in 13 industries (Asia-Pacific, North America, and Europe) revealed that 70% of them are already deploying or planning to deploy quantum-safe solutions in the next five years, with 65% being deeply concerned about “harvest-now, decrypt-later” attacks by future quantum attackers.
Quantum readiness is seen by many as a non-negotiable, not a choice, to ensure long-term data protection.
2. Real-World QKD Deployments
In April 2025, Toshiba Europe successfully sent quantum-encrypted messages through a 254 km commercial German telco network using standard fiber-optic facilities and room-temperature detectors, without the use of cryogenic equipment.
Such advances represent key steps toward viable, scalable enterprise deployment
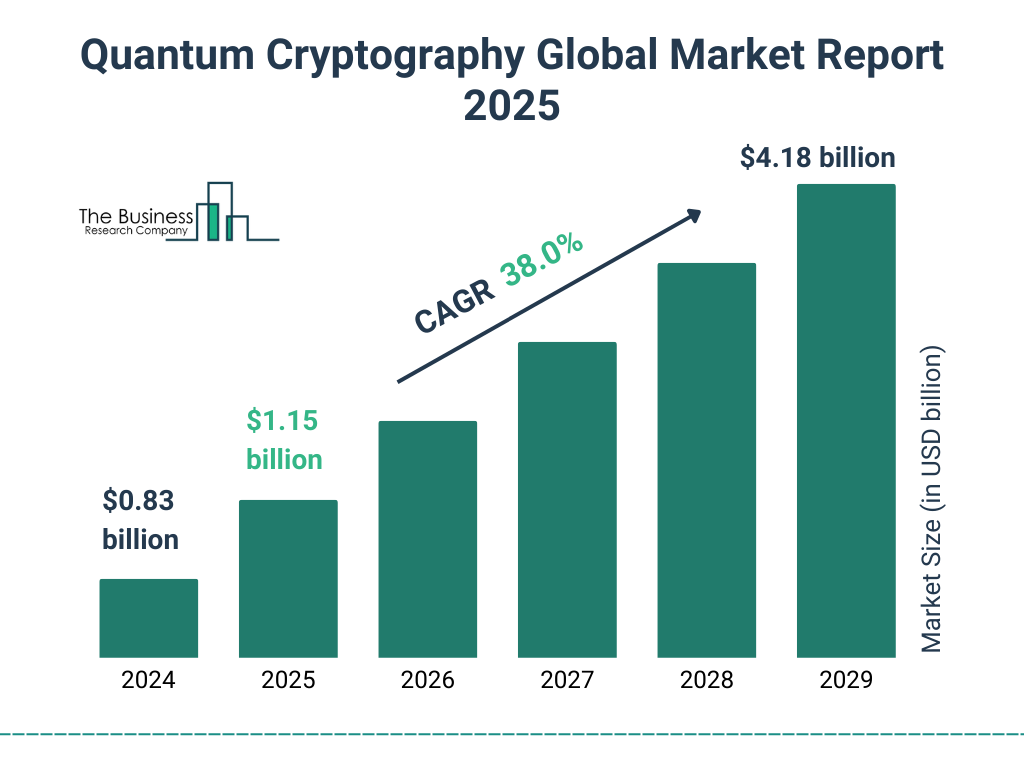
.3. Market Growth and Accelerating Investment
The worldwide quantum cryptography market expanded from approximately $1.16 billion in 2024 and is projected to grow to more than $4 billion by 2029, at a CAGR of ~38%
As equally important, early-stage quantum start-ups raised close to $2 billion in 2024, backed by robust public and private funding, and overall government investment reached more than $1.8 billion
4. Sector-Specific Adoption: Financial Institutions Lead
Financial institutions covered 42% of quantum security investment during 2023, and 67% of banks intend to move to quantum-resistant encryption by 2026
Increasing regulation and reputational risk make data confidentiality over the long term a business-critical priority.
With these present data points, the business case for quantum cryptography is apparent. That is, forward-looking investment, successful tests, and increasing enterprise interest are coming together to necessitate quantum-safe encryption as a strategic imperative.
Preparing for a Quantum-Secure Future
Quantum cryptography is more than a technological advance; it’s a paradigm shift in the way we conceptualize digital trust, resilience, and long-term data security. As quantum computing moves from abstract to concrete, threats to existing cryptographic systems will only become more urgent.
While execution is still complicated, visionary organizations and governments are beginning to implement quantum-safe measures combining Quantum Key Distribution, post-quantum algorithms, and forward-thinking security planning. For cybersecurity executives, waiting until quantum computers enter the scene is not an option; it’s time to act.
By knowing what quantum cryptography is, why it is important, and eventually how it can be used, CISOs and CIOs can better evaluate their company’s risk profile, get ready for future disruption, and keep data safe in the quantum world.
Frequently Asked Questions (FAQs)
1. Why should cybersecurity teams care about quantum cryptography?
Today’s encryption could be compromised by quantum computers. Cybersecurity teams need to get ready today to safeguard long-term sensitive information.
2. What’s the difference between quantum cryptography and post-quantum cryptography?
Quantum cryptography uses quantum physics for security. Post-quantum cryptography updates current encryption to resist quantum attacks.
3. Can businesses use quantum cryptography today?
Yes, but it’s still early. Some governments and large firms are testing it in secure communication networks.
4. Is quantum cryptography 100% secure?
It’s very secure by design, but poor implementation or hardware flaws can still create risks.
5. Which sectors will require it first?
Industries such as defense, finance, energy, and healthcare need to implement it first to safeguard important and long-term information.
For deeper insights on agentic AI governance, identity controls, and real‑world breach data, visit Cyber Tech Insights.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at sudipto@intentamplify.com.








