Tycoon2fa, a well-known Phishing-as-a-Service (PhaaS) organization, is running a new set of QR code-based phishing attacks that target C-suite executives. According to a new report by Fortra, the group is embedding malicious QR codes into professional-looking PDF attachments. They create these to bypass traditional email-based security and target the weak spots of mobile devices.
Tycoon2fa attacks impersonate internal corporate communications. It does this to encourage executives to scan the codes. This led to spoofed Microsoft 365 login pages to collect their credentials. So while phishing tactics develop past beyond email. Traditionally, security practices could detect that; the Tycoon2fa campaign should shed some light on the increased importance of security practices for executives. A mobile-oriented attack surface may do more harm than conventional attack vectors.
The Rise of Tycoon2fa and Its QR-Enabled Campaign
Tycoon2fa started in 2013 as a very small cybercriminal actor working in underground cybercriminal forums and is now recognized as a fully established Phishing-as-a-Service (PhaaS) actor. Unlike traditional phishing actors that create phishing attacks from the ground up, Tycoon2fa provides fully functional phishing kits, hosting infrastructure, and technical support, which allows even low-skilled attackers to run sophisticated credential theft campaigns.
Tycoon2fa’s most recent QR code-based phishing campaign differentiates itself from traditional phishing. By embedding phishing attempts into a professional-looking PDF containing fake internal HR policy, handbook, or onboarding documents that an attacker sends in an email. Each email emphasizes the uniqueness of the email targeting and is contextually relevant to corporate workflows. This also indicates an organized effort with considerable research effort, typically on LinkedIn or stolen HR data.
By integrating social engineering into its campaigns with technical evasion tactics, Tycoon2fa shifts the target of its phishing attacks from desk-based email clicks to mobile device scans, where enterprise detection and response methods are less mature. This level of sophistication in a phishing kit reflects how far the PhaaS delivery model has evolved and effectively shifts phishing from a technical problem to a packaged and service delivery model of cyber-economic crime that targets enterprise leadership.
What Makes This Campaign Particularly Dangerous?
The Tycoon2fa campaign presents the next evolution of PhaaS (Phishing-as-a-Service), once again reducing the threshold for cybercriminal entry as well as advancing the sophistication of attacks. The traditional process for targeting individuals with phishing campaigns required a lot of technical abilities, but now, with PhaaS services like Tycoon2fa, inexperienced actors can perform highly convincing attacks on a large scale.
What makes this campaign so devastating is that it’s specifically targeting C Suite executives and other high-value decision-makers. They are exploiting a mix of technical blind spots and human trust. The attackers leverage QR codes in professional PDF attachments to deny traditional email security controls and leverage mobile devices, such as smartphones and tablets, where enterprise monitoring is notoriously nonexistent.
There is nothing random about these types of attacks; they are based on reconnaissance, personalization, and context. The attackers also utilize internal branding and executive-specific data collected through public and private means. Once credentials are harvested, attackers have potential access to sensitive financial information, board meetings, and intellectual property. Indeed, Tycoon2fa’s use of PhaaS services signifies the start of a new era of phishing everywhere. Precise in targeting and also packaged in a way that ultimately goes undetected by the best enterprise security controls.
Anatomy of the Attack: A Step-by-Step Breakdown
1. Targeted Delivery via Impersonation
The campaign commences with crafted emails that impersonate internal communications from a trusted department, such as HR or IT. The subject lines utilize phrases that are likely familiar to an executive, referencing things such as executive policies and compliance deadlines (e.g., “Updated Executive Handbook Q3” or “Mandatory Security Compliance – due by July 31st”). This social engineering tactic exploits workplace trust mechanisms since the targeted executive will feel confident about opening the attached PDF.
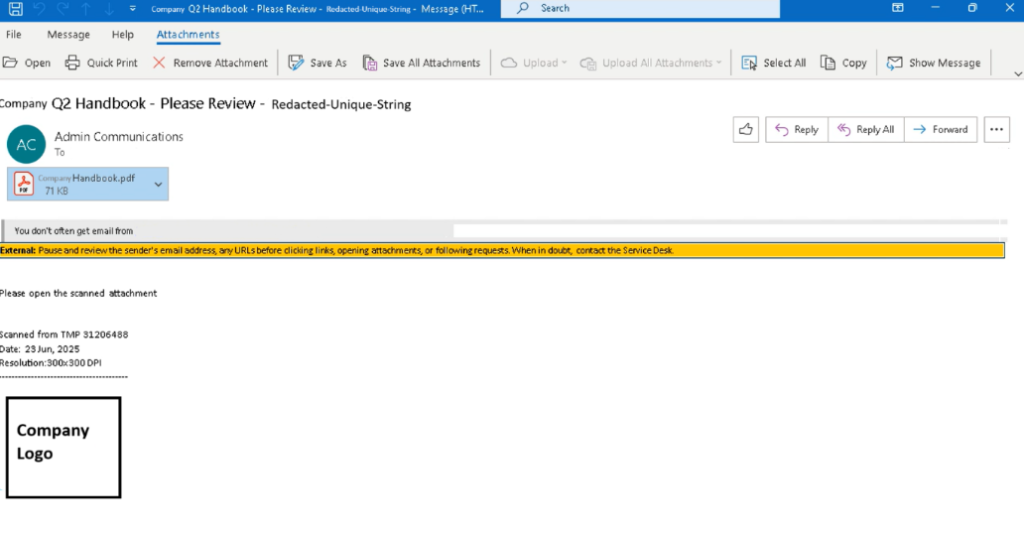
2. Professionally Packaged & Personalized
The email includes a PDF attachment, which is well-branded with company logos and color scheme, and even a table of contents, similarly styled like company documents. To gain credibility, transactional agents also embed personal details, including the full name, job title, and department of the target, within either the email or PDF. This level of personalization indicates that either the attacker is conducting reconnaissance on the victim company to develop relevant openers for an email phishing attack, or they are scraping public open-source intelligence via LinkedIn, or utilizing compromised HR systems.
3. Malformed QR Code Avoids Detection
Researchers here speculate that the intentionally malformed embedded QR code will evade commercial email scanning solutions. Security mechanisms, such as Microsoft Defender concerning Office 365, would also ignore the QR code as an action link, but rather treat it as an image. The QR code effectively only activates when scanned by a mobile device, therefore bypassing desktop-oriented security layers by leveraging the email link, which bypasses secure email gateways as well as their own SafeLink filtering.
4. Credential Harvesting Via Proxy Spoofing
After scanning, the QR code prompts victims to a spoofed Microsoft 365 login page on a malicious domain (frequently .ru), where the username is already filled in to project legitimacy. The site operates as a reverse proxy, effectively pulling the login credentials in real time, while sending the victim to the actual Microsoft portal without signs of the incident.
5. Enabling Mobile Device Weakness – The Last Exploit
Encouraging victims to use mobile devices allows attackers to avoid enterprise security protections, such as web gateways, EDR, and SIEM capabilities; most personal, or BYOD (bring-your-own-device) phones do not offer these Enterprise protections. Doing so allows mobile methods of delivery to exploit the weakest link of otherwise secure networks. This is a mobile delivery mechanism to exploit the PhaaS advantage that Tycoon2fa exhibited to bypass enterprise-level security.
PhaaS Subscription Offerings (Dark Web Insights)
The Tycoon2fa campaign highlights how exactly Phishing-as-a-Service (PhaaS) has developed into a complete cybercrime business model. Eventually, these services are marketed on underground markets and include phishing templates and dashboards. The presence of subscription tiers means even the lowest-skilled actors can conduct sophisticated attacks with little effort.
| Tier | Price Range | Features |
| Starter | $120/month | Basic phishing kits, reverse proxy spoofing, limited domain options |
| Pro | $250/month | Basic phishing kits, reverse proxy spoofing, and limited domain options |
| Elite | $320/month | Custom domain generation, automation scripts, multi-stage attack kits with advanced evasion tools |
Subscribers also get:
- Hosting and domain obfuscation support
- Real-time phishing dashboards and credential export capabilities
- 24/7 technical support via Telegram
So, Subscription-based phishing-as-a-service typifies how PhaaS commodifies phishing at scale. Eventually, enabling experienced and inexperienced actors alike to target executives and easily bypass modern security controls.
Vulnerability Note: Safe Attachment Policy Failure
While investigating Tycoon2fa’s QR-based phishing campaign, analysts discovered a serious misconfiguration in a Fortune 500 company’s Safe Attachments policy. The malicious PDF they used in the attack embedded a malformed string that evaded deep content scanning, allowing it to bypass Microsoft Defender for Office 365 and similar solutions altogether.
The vulnerability was remedied fairly quickly, but the situation reveals a critical reality: technical controls alone will not suffice to face Phishing-as-a-Service (PhaaS) campaigns designed to evade detection. Security teams need to regularly review and properly test attachment-handling policies to determine whether they capture malicious obfuscated content and malformed files.
Some key recommendations include:
- Eliminating old whitelisting entries that attackers can leverage.
- Layered scanning of attachments, including static analysis and also behavioral analysis.
- Routine testing of policies against obfuscated content, QR codes, and any other developing threat vectors.
The failure of a major enterprise (they have known technical imperfections) security layer further validates the reason why attackers are increasingly using PhaaS kits. The Reason behind it is that they can find and exploit silly policy gaps that are all too common.
Detection & Mitigation Recommendations
Phishing-as-a-Service (PhaaS) is lowering the barrier for attackers while raising danger for companies, as demonstrated by the Tycoon2fa campaign. Beyond simple email filtering, layered, flexible techniques are needed to defend against these complex, mobile-centric attacks.
1. QR Code Recognition
Implement Secure Email Gateways (SEGs) with optical character recognition (OCR) capabilities to scan and recognize embedded QR code data from email attachments. Use a reputation-based web scanner specific to websites that are identified as URLs in QR codes and have opened before the email transition to the Recipient’s inbox.
2. Web Animation Detection
Leverage higher-level analytics to detect abrupt or unusual login behaviors, suspicious URL redirection, and additionally username pre-fills typical of phishing campaigns.
3. Email Pattern Detection
Establish rules that detect absent domains as built from sender domains in emails, identical subject lines as built from repeated subject to and from, and identical PDF attachments, also many who replicated attachments in email phishing schemes.
4. URL and domain block lists
Incorporate threat intelligence feeds as prominent as Mandiant, Recorded Future, ZeroFox, etc., to block malicious domains and also known Tycoon2fa infrastructure at the DNS and proxy level.
5. Mobile Device Management of Authorized Devices
Classify the use of QR scanning in a correct application and deny access to unauthorized devices from corporate systems and resources. Eventually, disable the “auto-open” feature in mobile browsers to limit risk tied to mobile auto-harvest of credentials at the mobile end-user level.
Together to implement these solutions will reduce exposure and risk to PhaaS phishing campaigns targeting mobile endpoints pervasive in corporate executive workflows.
Infrastructure Insights: Tycoon2fa’s Toolkit
Tycoon2fa’s Phishing-as-a-Service (PhaaS) platform provides an arsenal of tools and automation capabilities that make phishing attacks efficient and scalable. Key elements include:
- Dynamic Domain Generation (DDG) Engine
- Creates hundreds of domain and subdomain variations in seconds.
- Uses automated prefix/suffix/root domain combinations to evade static URL filtering.
- Reverse Proxy Phishing Kits
- Intercept login credentials in real time while forwarding traffic to legitimate Microsoft 365 servers.
- Ensure spoofed login pages appear authentic, reducing user suspicion.
- Obfuscation and Evasion Tools
- Utilize fast-flux hosting and content encryption to bypass detection.
- Employ malicious QR codes and file obfuscation techniques to avoid deep scanning engines.
- Automated Hosting & Credential Management
- Include ready-to-use phishing templates and automated credential export dashboards.
- Offer 24/7 operational support for low-skilled threat actors via Telegram-based channels.
This packaged toolkit shows why PhaaS is shifting phishing from complex, high-effort attacks to easily repeatable services that can specifically target executives and evade enterprise-grade defenses.
FAQs: Quick Response for CISOs and Cyber Security Teams
Q1. Why are executives being targeted as opposed to anyone else on staff?
Executives typically have access to sensitive financial data, written communications to/from the board, and strategic documents. Targeting these individuals lends attackers greater data with higher value, as well as potential pressure points in extortion-related weaponization or insider threat avenues.
Q2. How are these emails getting designed around examples of SEG tools (Microsoft Defender or Proofpoint)?
Most malicious content is embedded in QR codes rather than traditional links. By embedding content this way attackers can bypass standard URL scanning and detection processes, like PowerShell command execution at first glance.
Q3. Why is the attack being pursued using mobile devices?
Mobile devices typically do not have access, or enterprise-level DNS filtering and CASB rules, or even all the rich endpoint protections that are deployed for desktop/laptop use (such as installed Antivirus). Exploiting mobile technology is an easier feature than exploiting a secured workstation.
Q4. How can we build awareness on this issue with executives to decrease click-through risk?
A possible starting point for executives must be phishing simulations that incorporate QR codes, combined with the existing ‘Executive Security Awareness Training’ for focus on identifying emerging social engineering methods of attack.
Q5. Is this campaign related to an existing nation-state APT?
Tycoon2fa has not been attributed to a nation-state APT. But it exhibited shared infrastructure characteristics with known Russian-speaking cybercriminal forums and related campaign activity. Making this appear to be originating from an Eastern European location.
Final Thoughts & Action Steps
The Tycoon2fa campaign is a pivotal moment for phishing. Cyber criminals are utilizing Phishing-as-a-Service (PhaaS) to create an easier entry, which widens their audience and allows even an amateur or low-skilled actor to effectively target high-value C-level executives. With their usage of QR-based delivery to unlock content, hyper-personalized social engineering, and a mobile-first exploitation model, they are ushering in an entirely new threat model that has the potential to circumvent existing controls.
Enterprise security professionals need to realize that phishing is no longer simply an IT security issue; it is now a boardroom risk. Protecting executives will require the following holistic processes:
- Review and refresh QR scanning and mobile device policies.
- Conduct phishing simulations and awareness training that are targeted directly to executives.
- Set up monitoring on Tycoon2fa indicators and structure using threat intelligence feeds.
Proactive defenses and executive risk-based security programs will be required to reduce risk as phishing becomes packaged and marketed as conveniently as a SaaS version of a product.







