In today’s digital world, your systems are only as strong as the weakest link in your supply chain. Even the most secure organizations can face breaches through vendors or third-party software they rely on. By 2025, 60% of supply‑chain organizations will use cybersecurity risk as a significant determinant in conducting third‑party transactions. A 2025 survey found that 79% of companies oversee less than half of their third-party suppliers– the vendors of their vendors. That’s a lot of potential exposure. So, how do you detect supply chain vulnerabilities before hackers do?
What Are Supply Chain Vulnerabilities?
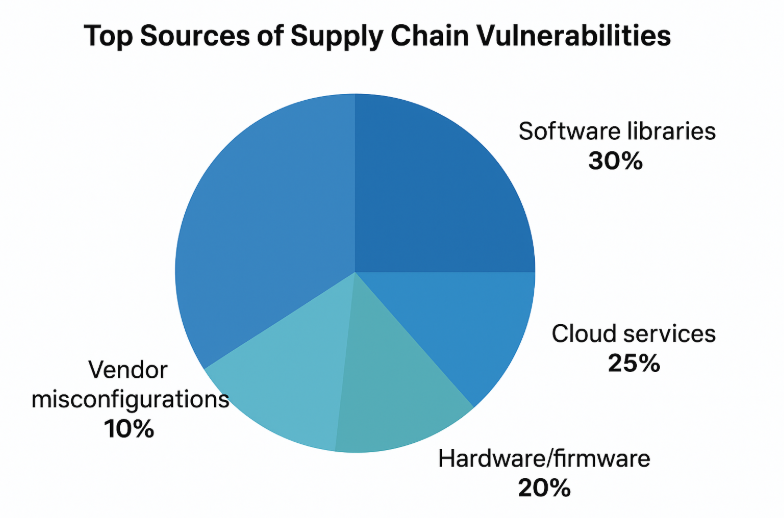
A supply chain vulnerability arises when a vendor, software component, or service provider introduces a potential point of compromise. Think of it as an unseen door into your system. It could be a flawed software library, a misconfigured cloud service, or a compromised firmware update. Attackers exploit these gaps to gain access, often without ever touching your direct systems.
Supply chain attacks take this a step further: instead of targeting your organization directly, attackers compromise a trusted vendor or software provider to infiltrate multiple downstream systems. For example, a malicious update in an open-source library or a compromised vendor server can silently spread malware to all clients relying on that service. These attacks are increasingly common and can affect thousands of organizations simultaneously, making them highly efficient and dangerous. According to a survey, supply chain attacks are expected to be a primary source of cybersecurity incidents for organizations globally.
Why They Often Go Unnoticed
- Limited visibility: Many companies track direct suppliers but overlook their vendors’ vendors.
- Rapid innovation: Open-source libraries and fast development cycles create new dependency points.
- Human factors: Even the best teams may overlook updates or vendor changes when deadlines loom.
In short, vulnerabilities hide in plain sight. Detecting them requires proactive strategies, not just hope.
In a McKinsey survey, just under half of respondents said they understood the location of their tier‑one suppliers and key risks; only 2% could say the same about third-tier and beyond.
Steps to Detect Vulnerabilities
1. Map Your Supply Chain
Create a clear inventory of vendors, third-party services, and dependencies. Identify critical vendors with access to sensitive systems. Assign owners to each vendor for accountability.
2. Define Vendor Security Baselines
Set minimum security requirements: encryption, endpoint protection, incident reporting, and software update practices. Require vendors to attest to compliance and provide proof.
3. Monitor Dependencies and Workflows
Use tools to scan software dependencies for vulnerabilities. Track changes in CI/CD pipelines and alert teams to unusual updates or versions. For hardware, maintain a bill of materials and verify firmware integrity. 72% of respondents say cyber risks have risen in the past year, and growing ecosystem inter‑dependencies increase risk.
4. Conduct Regular Risk Assessments
Evaluate vendors’ risk levels annually or quarterly for critical suppliers. Include questionnaires, audits, and proof of penetration testing or patching schedules. Adjust risk ratings as relationships or vendor environments change.
5. Watch for Early Warnings
Track vendor announcements, unusual downtime, delayed patches, or news of third-party breaches. Subscribe to threat intelligence feeds focusing on software and hardware supply chains.
6. Prepare Response Strategies
Develop an incident response plan for vendor-related breaches. Limit vendor system access using least-privilege principles and run tabletop exercises simulating supply chain attacks.
Key Takeaways
- Visibility is essential: Know all critical vendors and their dependencies.
- Set clear security standards: Ensure vendors meet them and provide proof.
- Monitor and scan continuously: Detect issues before deployment.
- Assess risk regularly: Treat vendor security as ongoing, not one-time.
- Act proactively: Early detection plus preparation is your best defense.
Conclusion
Supply chain vulnerabilities are no longer hypothetical- they are a real and present risk for every organization. By proactively mapping your vendors, setting clear security standards, continuously monitoring dependencies, and conducting regular risk assessments, you can detect weaknesses before attackers do. Early detection, paired with a well-prepared response strategy, transforms your supply chain from a potential liability into a resilient, secure asset. In cybersecurity, being proactive isn’t optional- it’s the difference between staying ahead of threats and reacting after the fact.
FAQs
Q1. What signals indicate supply chain vulnerabilities?
Delayed patches, sudden version changes in software libraries, or vendors not providing transparency.
Q2. Are only software vendors a risk?
No. Hardware, firmware, cloud services, and even logistics vendors can introduce vulnerabilities.
Q3. How often should vendor risk be reviewed?
Annually for most vendors, quarterly for critical ones, or after significant changes.
Q4. Which tools help detect supply chain risks?
Software composition analysis (SCA), CI/CD monitoring, vendor audits, and threat intelligence feeds.
Q5. Can contracts alone protect against supply chain risks?
No. Contracts must be paired with audits, monitoring, and operational enforcement.
Don’t let cyber attacks catch you off guard – discover expert analysis and real-world CyberTech strategies at CyberTechnology Insights.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at info@intentamplify.com.








