Cyber attacks are sophisticated, targeted, and more often aimed at chief executives in today’s digital-first business landscape. Spear-phishing is one of the most subtle types of attack. It is crafted to take advantage of legitimacy to obtain access to confidential business information, financial systems, and intellectual property.
In contrast to the generalized net of regular phishing, spear-phishing targets specific individuals, frequently following intense research. B2B companies can suffer significant financial losses, regulatory fines, and reputational damage from just one successful attack. The senior executives need to understand the threat and take basic, proactive steps to defend their organizations.
What is Spear-Phishing?
Spear-phishing is a type of cyber attack where criminals create highly personalized messages. These messages target a specific person or group of people. Unlike phishing messages that thousands of people receive and send out blindly, spear-phishing messages are specific and have escaped regulations; sometimes they even include personal or company information to gain credibility. The attacker can impersonate the email address of an executive, refer to company projects, or name trusted partners.
The goal is to trick the target into taking an action. Such as clicking on a bad link, downloading malware, or transferring wire money. This focused technique makes it powerful and hazardous in a B2B environment, where critical business activities are concerned.
Why Executives Are Targeted in B2B Cybersecurity
Executives are targets of choice since they possess strategic information, money, and decision-making capabilities. The attackers seek to leverage these privileges to conduct business email compromise (BEC) activities. They also steal intellectual property or cause operational disruption. For instance, finance teams and CFOs are often the targets of bogus invoice requests. This initiates fraudulent wire transfers. High-profile incidents, such as the social engineering attacks on the boards of well-known companies. These demonstrate how quickly spear-phishing may result in losses of millions of dollars. In addition to causing monetary loss, a breach damages brand reputation, erodes stakeholder trust. And may result in regulatory penalties in sectors including healthcare and finance.
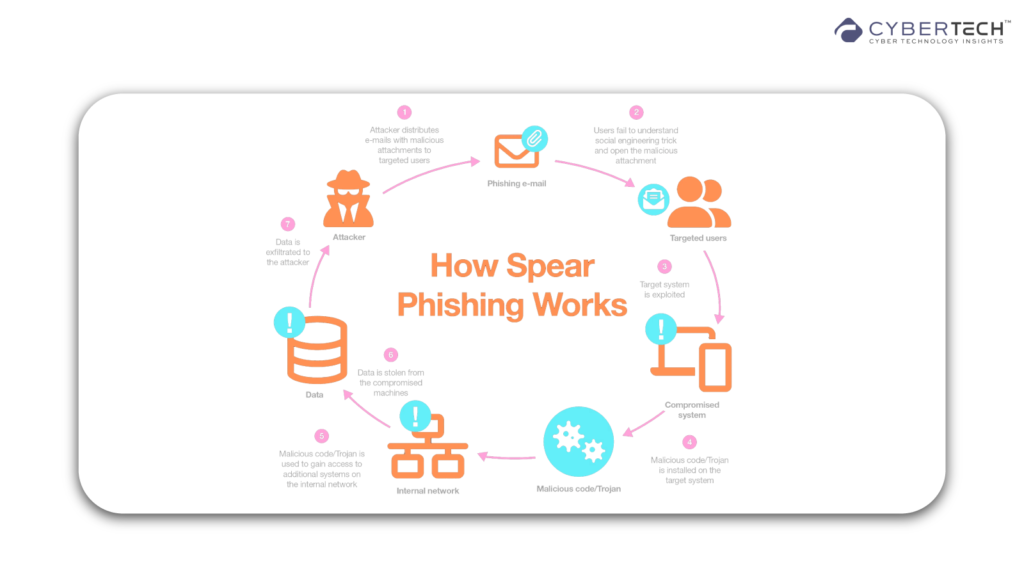
The Psychology Behind Spear-Phishing Attacks
Spear-phishing is highly dependent on social engineering. The attackers take advantage of human psychology. Trust, urgency, and authority pressure to force the recipients to act. They usually carry out a thorough reconnaissance of LinkedIn profiles, press releases, or corporate directories to develop persuasive messages. Busy executives, with multiple responsibilities and constantly bombarded by urgent messages, are an easy target. A message that bears the semblance of a trusted colleague or partner can easily escape critical scrutiny. This blending of targeted research and psychological deception is what separates it from mass phishing attacks and makes it such a serious risk to enterprise executives.
Standard Methods Utilized in Spear-Phishing
Similarly, spear-phishing assaults employ a variety of tactics to bypass traditional security mechanisms. Understanding how they work, as well as real-world instances, enables executives and security experts to recognize and protect against these dangers.
Business Email Compromise (BEC):
In BEC attacks, scammers impersonate executives, suppliers, or long-time business partners to authorize suspicious transactions. In one widely reported example in 2020, a U.S.-based technology company lost $2.3 million after attackers spoofed emails from the CEO that sounded to the finance department as if the CEO was asking them to wire funds to an international account.
The emails were well written to match the executive’s writing style and tone – without independent verification, the finance department, or sender, may not detect that it is a fraudulent or spoofed email. According to the FBI Internet Crime Complaint Center (IC3), BEC scams from December 2022 through December 2023 accounted for reported losses of over $55 billion globally.
Fake Invoice Scams:
Attackers often target finance teams with authentic-looking invoices. An old example is when a European manufacturing company was sent an invoice that was almost the same as its normal supplier invoices, but with the bank account information changed. The finance department almost forwarded €350,000 before detecting a problem in the account number. Such scams are based on knowledge of business operations and internal approval cycles.
According to Keenpet Labs Statistical data in 2024, phishing emails represented 1.2% of all emails sent worldwide, which translates to 4 billion phishing emails per day.
Malware Attachments and Links:
Spear-phishing emails often include attachments or links that launch malware or ransomware. For example, attackers sent emails to a US energy business posing as regulatory letters, with a PDF attachment carrying malware. Once opened, the malware granted attackers remote access to internal computers, exposing key operating information.
Current efforts increasingly use AI to customize communications based on the recipient’s function, making it more likely that they will click on questionable links. In Q1 2025, the Anti-Phishing Working Group (APWG) recorded more than 1 million phishing attacks, the most since late 2023.
Credential Harvesting:
Threat actors create impostor login websites that closely resemble corporate networks or cloud services, convincing executives to enter their identities and passwords. A 2024 report claims that spear-phishing attempts are responsible for 66% of breaches but only 0.1% of all email-based phishing attacks.
For instance, the CISO of a financial company was notified via email that their Microsoft 365 account required validation. They were sent to a fake login page by the link, which allowed hackers to obtain sensitive email accounts without authorization. These methods are always changing. Attackers now use AI and automation to create extremely credible messages, add multi-channel strategies, and even use pop events or executive travel plans to have a better chance of success. By learning from these examples, businesses can more effectively predict attacks and build stronger defenses.
Preventing it in B2B organizations.
Spear-phishing must be tackled with a comprehensive combination of technology, process, and human understanding.
Executive Awareness and Training: Executives must receive training in spotting dubious messages through simulated phishing, minimizing the likelihood that they may unwittingly compromise the firm.
Multi-Factor Authentication (MFA): Phishing-resistant MFA solutions such as hardware tokens and FIDO2 security keys are a required second factor of protection.
Email Security Solutions: Advanced email filtering, secure email gateways, and AI-based threat prediction detection will do the legwork, marking suspect communications before they reside in the inbox.
Strong Verification Processes: Finance groups must be using a dual approval process for wire transfers, as well as cross-verify requests using a different method of communication.
Incident Response Planning: Companies must have a definitive process to contain a breach, such as quickly quarantining the compromised account and containing the breach as soon as possible, including notifying regulators or authorities in given events.
Using these steps in concert is likely to greatly reduce the risk of spear-phishing aimed at executives and high-value targets for B2B companies.
Conclusion
Spear-phishing is a changing and serious threat to the B2B cybersecurity sector, targeting executives in charge of very valuable assets and sensitive data. There are only three ways to combat spear-phishing, which are: awareness, technology, and discipline. It is not enough to rely solely on technical defenses. Executives and employees have to have education, validation procedures, and incident response plans to mitigate spear-phishing attacks. As long as a company has these three actions in place, it can mitigate the risk of financial loss, damage to reputation, and breach of stakeholder trust. Knowing and defending yourself against spear-phishing is a business requirement, not an IT requirement.
FAQs
What makes spear-phishing different from what might be considered normal phishing?
It is precisely targeted and personalized, while typical phishing is more mass-message emails and casts a wide net. Spear-phishing is targeted at certain persons or departments.
Why are executives the main targets?
They are the main target because Executives have strategic information and budget authority. In addition to that, they also have decision-making capabilities.
What should I do if I receive a spear-phishing email?
Do not click on any links or open attachments. Email the spear-phishing email to your IT/security team immediately, and if there are any urgent requests to confirm through another method.
Can technology protect against these types of attacks by itself?
No. Email filters and MFA reduce risk, but the attackers trigger human action. Awareness training and cross-authentication methods are needed to take as a countermeasure.
How often should executives receive awareness training?
Quarterly, and preferably with simulated attacks to reinforce the use of recognition and also response security behaviors with suspicious messages.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at sudipto@intentamplify.com.







