New Report finds DarkSpectre Malware Compromised 8.8 Million Browsers Through Trusted Extensions
Security researchers have uncovered one of the most quietly successful browser-based malware campaigns ever documented. Dubbed DarkSpectre, the threat actor infected more than 8.8 million users by weaponizing trusted browser extensions across Chrome, Microsoft Edge, and Firefox, remaining undetected for nearly seven years.
The findings, published by Koi Security, expose a troubling reality for modern cybersecurity technology teams: browser ecosystems—long treated as low-risk productivity layers—have become high-value targets for advanced threat actors.
“DarkSpectre infected over 8.8 million users in over seven years of operation,” Koi researchers stated, highlighting the unprecedented scale and persistence of the campaign.
How the Investigation Expanded Beyond Initial Findings
Following the publication of its initial ShadyPanda research, Koi Security expanded its investigation to deepen indicator-of-compromise (IOC) analysis and infrastructure mapping. What researchers expected to be a small number of additional related extensions quickly escalated into something far larger.
“After publishing our initial ShadyPanda investigation, we went back to expand our IOC research. We expected to find a few more connected extensions. We found over 100,” Koi researchers stated.
The breakthrough came from pivoting on two domains identified in the original report—infinitynewtab[.]com and infinitytab[.]com. Those domains acted as critical infrastructure anchors, allowing investigators to trace shared backend services, publisher relationships, and communication patterns across dozens of seemingly unrelated browser extensions.
This expansion confirmed that DarkSpectre was not operating isolated campaigns, but rather maintaining a coordinated, centrally managed extension ecosystem designed for long-term persistence and large-scale browser compromise.
Weaponizing Trust at Scale
Unlike traditional malware operations that rely on exploits or phishing, DarkSpectre took a more disciplined—and more dangerous—approach. The group published fully functional browser extensions that appeared legitimate, passed marketplace reviews, and delivered genuine utility to users.
Extensions offered features such as:
- New tab dashboards
- Productivity widgets
- Customizable layouts
Domains like infinitynewtab[.]com and infinitytab[.]com hosted these services, reinforcing user trust. But behind the scenes, those same extensions quietly communicated with separate command-and-control (C2) infrastructure, enabling malicious activity without raising alarms.
This dual-use design allowed DarkSpectre to blend seamlessly into trusted systems—an increasingly common pattern in modern IT and security threats.
Three Campaigns, One Operator
Through infrastructure correlation and behavioral analysis, researchers identified three distinct campaigns operated by the same entity:
- ShadyPanda – ~5.6 million infected users
- Zoom Stealer – ~2.2 million infected users
- GhostPoster – ~1.05 million infected users
Each campaign appeared independent at first. However, shared backend infrastructure, overlapping publisher accounts, and reused tooling ultimately revealed a centrally managed operation.
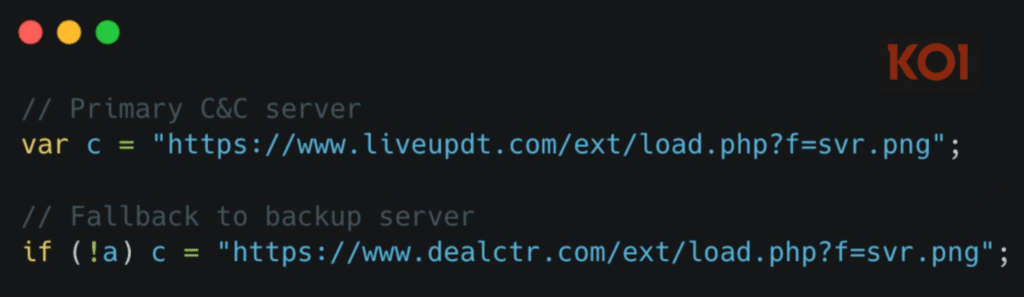
Image source: KOI AI
Researchers described the investigation as piecing together a sprawling and evolving threat network—“unraveling a web of interconnected extensions, publishers, and domains”—a structural complexity reminiscent of supply-chain and APT campaigns that modern detection platforms like Darktrace flag through behavioral anomalies rather than traditional signatures, as these stealthy threats increasingly blend into trusted systems.
Why DarkSpectre Stayed Undetected for Years
DarkSpectre’s longevity was not accidental—it was engineered.
Time-Bomb Activation
Several extensions remained dormant for days, weeks, or even years after installation. One extension, New Tab – Customized Dashboard, delayed malicious activity for three days, allowing it to pass automated and manual marketplace reviews.
Selective Execution
Malicious behavior activated on only ~10% of page loads, drastically reducing detection during sandbox testing or analyst review.
Steganographic Payload Delivery
Rather than serving obvious scripts, DarkSpectre hid encoded JavaScript inside PNG image files, which appeared to be harmless extension assets. Once extracted, the payload executed silently in the background.
Heavy Obfuscation
The malware used:
- Custom encoding
- XOR encryption
- Packed and layered JavaScript
This combination defeated signature-based detection and slowed reverse engineering.
Server-Side Control Model
Perhaps most critically, DarkSpectre shifted malicious logic to backend infrastructure. Extensions dynamically downloaded encoded scripts from attacker-controlled servers, allowing operators to change behavior without issuing extension updates.
This approach renders traditional extension takedowns and signature blocking largely ineffective.
Browser Extensions: The New Supply-Chain Risk
The DarkSpectre campaign underscores a critical shift in the threat landscape. Browser extensions now operate as mini supply chains, executing persistent code inside trusted user environments with broad permissions.
For IT and security leaders, this represents a blind spot—one where malware can:
- Steal session cookies or tokens
- Inject scripts into web traffic
- Monitor browsing behavior
- Maintain long-term access without triggering endpoint alerts
As attackers increasingly abuse legitimate platforms, defenders must assume that trust itself is now an attack surface.
Reducing Browser Extension Risk in Enterprise Environments
Security researchers emphasize that mitigating extension-based threats requires layered controls, not reactive cleanup.
Recommended best practices include:
- Audit and inventory all installed extensions, enforcing strict allowlists and least-privilege permissions
- Centralize browser and extension management through enterprise policies controlling installs, updates, and removals
- Monitor browser behavior for anomalies such as delayed activation, unusual network traffic, or dynamic payload loading
- Apply zero-trust and conditional access controls to browser sessions
- Strengthen identity and session protections to reduce the impact of stolen cookies or tokens that bypass MFA
- Educate users on extension risks and maintain long-term logging and threat hunting to detect slow-moving threats
Collectively, these controls improve visibility while limiting the blast radius of compromised extensions.
Why Trusted Systems Are Now Prime Targets
DarkSpectre is not an outlier—it is a signal.
Threat actors are increasingly abandoning noisy exploits in favor of long-dwell persistence within trusted systems. Browser platforms, SaaS integrations, and software marketplaces provide adversaries with durable footholds that blend into daily workflows.
This evolution challenges traditional cybersecurity assumptions and reinforces the need for zero-trust security models that continuously verify behavior, not just identity.
As threats hide in plain sight, organizations that fail to treat browsers as critical infrastructure will remain exposed—often for years—without realizing it.
FAQs
1. What is DarkSpectre malware?
DarkSpectre is a long-running malware operation that abused legitimate browser extensions to compromise users at scale. Instead of exploiting vulnerabilities, it leveraged trusted extension marketplaces to maintain stealthy, long-term persistence across Chrome, Edge, and Firefox.
2. How did DarkSpectre infect 8.8 million browsers without being detected?
The campaign relied on delayed activation (“time-bomb” techniques), selective execution on a small percentage of page loads, heavy JavaScript obfuscation, and server-side payload delivery. This allowed malicious extensions to pass security reviews and evade traditional signature-based defenses.
3. What risks did DarkSpectre pose to users and enterprises?
Infected extensions could potentially monitor browsing behavior, inject malicious scripts into web sessions, steal cookies or authentication tokens, and maintain persistent access within trusted browser environments—often without triggering endpoint security alerts.
4. Why is this campaign significant for cybersecurity and IT leaders?
DarkSpectre demonstrates that browser extensions now represent a serious supply-chain and trust-based attack vector.
As highlighted in coverage by CyberTech Insights, the campaign reinforces how attackers increasingly hide inside trusted systems, bypassing traditional perimeter and endpoint controls.
5. What lessons should organizations take away from the DarkSpectre investigation?
Organizations must treat browsers as critical infrastructure. This includes enforcing strict extension allowlists, applying least-privilege permissions, centrally managing browsers, monitoring extension behavior, and adopting zero-trust security models that continuously verify access rather than assuming trust.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at info@intentamplify.com.






