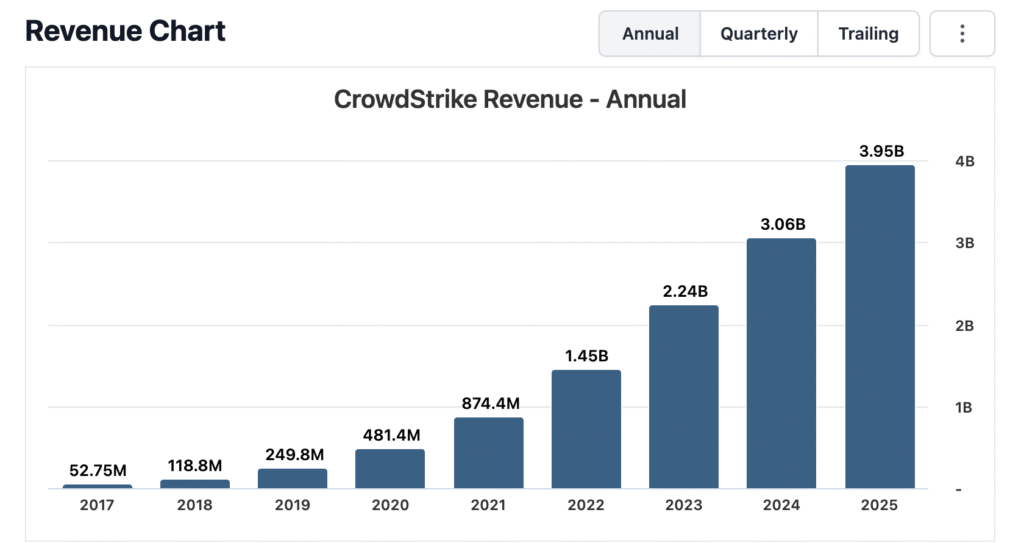
Earlier this week, cybersecurity giant CrowdStrike reported annual revenue approaching $4 billion, with ARR growing over 20% year-over-year, underscoring strong enterprise demand for comprehensive digital protection.
In that context, CrowdStrike’s agreement to acquire Seraphic Security is not a routine M&A announcement—it marks a decisive inflection point in how enterprises must secure work as applications and AI-driven activity converge inside the browser.
Browser Security Is No Longer Simple — or Optional
As browser usage explodes across SaaS, cloud apps, and AI tools, the attack surface has quietly expanded. But securing that surface without breaking productivity is far from trivial.
Hank Thomas, Co-founder and CEO of Strategic Cyber Ventures, captures the challenge succinctly:
“The move highlights how critical browser security has become, but it’s a complex space. Securing sessions across multiple browsers without disrupting performance or user experience is challenging. Success will depend on seamless integration with existing Zero Trust and identity frameworks. Worth watching how well it reduces real risk without adding friction for enterprises.”
His point underscores a hard truth: browser security only works if users barely notice it. Any added friction risks shadow IT, workarounds, or outright failure.
Why This Acquisition Matters to the Market
For years, browser security sat on the periphery—often treated as an extension of endpoint protection or web gateways. That era is ending.
Pejman Roshan, Chief of Strategic Initiatives at Menlo Security, frames the acquisition as market validation rather than surprise:
“CrowdStrike’s move confirms what Menlo Security led the market in asserting: traditional endpoint and network security are no longer enough, because the browser is now how we access applications, data, and AI resources.”
When the world’s largest endpoint security provider steps into browser security in a meaningful way, it sends a clear signal: the browser has become the enterprise’s most critical—and vulnerable—workspace.
The Browser as the New Enterprise Execution Layer
Roshan goes further, connecting the acquisition directly to AI-driven change inside enterprises:
“When the world’s largest endpoint security company acquires a browser security startup, it proves that the browser is now the most critical – and vulnerable – workspace in the enterprise, with the new demands of AI.”
As generative and agentic AI capabilities are embedded directly into browsers, security controls can no longer live outside the environment where work happens. They must be native, contextual, and continuous.
This is why, according to Roshan, the acquisition reinforces a growing enterprise preference:
“This wave of investment in browser security validates a new reality, that security must be native to every browser that employees and contractors already use, not locked inside a single replacement browser that users fight or workaround.”
In other words, “rip-and-replace” browser strategies are losing favor. Enterprises want control layers that sit on top of existing browsers—aligned with where users already work.
Control Layers Over Replacement Strategies
The logic is pragmatic. If enterprises could standardize on a single browser, many would have already done so. Instead, Chrome, Edge, and other browsers coexist—now with embedded AI features that promise major productivity gains.
Roshan notes:
“CrowdStrike’s acquisition of Seraphic validates that enterprises favor control layers on top of their existing browsers over rip & replace strategies because it aligns with where their users are already working.”
This approach also anticipates the next wave of AI-enabled browsers, where productivity gains will be inseparable from new security risks.
Validation — With Open Questions
For Menlo Security customers, this acquisition doesn’t change strategy—it confirms it:
“Our customers have known for years what this acquisition now confirms: the browser is not just another app, it is the enterprise’s primary execution layer.”
However, Roshan also points out what’s missing from the conversation so far:
“As the security and AI landscape evolves, it stuck out that CrowdStrike is not tying mentions of agentic AI into a coherent strategy or explanation of how the acquisition will allow them to solve specific agentic AI challenges.”
What’s notably absent is a clear articulation of how this acquisition changes CrowdStrike’s ability to secure agentic AI behavior inside the browser—not just human users. As AI agents increasingly execute tasks, move data, and make decisions autonomously within browser sessions, the security challenge shifts from monitoring access to governing intent, autonomy, and downstream actions. Acquiring browser visibility is a necessary step, but without a defined strategy for controlling agentic workflows, enforcing policy on autonomous actions, and detecting AI-driven misuse in real time, the acquisition risks being perceived as tactical rather than transformational.
What Comes Next
CrowdStrike’s acquisition of Seraphic marks a pivotal acknowledgment: securing endpoints alone is no longer enough. The browser is now the front line of enterprise execution, collaboration, and AI interaction.
The next chapter will hinge on execution—how seamlessly browser security integrates with Zero Trust and identity frameworks, how well it scales across browsers, and whether it can reduce real-world risk without slowing users down.
One thing is clear: browser security has moved from “nice-to-have” to strategic control point. And with AI accelerating inside the browser, the rest of the cybersecurity industry is now racing to catch up.
Our in-house analysts at CyberTech Insights predict that within the next 12–18 months, browser security will emerge as the primary control plane for enterprise cybersecurity, eclipsing standalone endpoint defenses. Vendors that fail to natively secure AI-driven workflows and agentic activity inside mainstream browsers will be forced into defensive acquisitions—or risk rapid irrelevance as the browser becomes the true operating system of the modern enterprise.
FAQs
1. Why is the browser becoming a strategic security control point for enterprises?
The browser has evolved into the primary interface for accessing SaaS applications, sensitive data, cloud services, and AI tools. As work shifts away from traditional desktops and on-prem systems, security controls must move closer to where execution actually happens—inside the browser—rather than relying solely on endpoints or network perimeters.
2. How does AI change the browser security risk profile?
AI introduces autonomous and semi-autonomous behavior directly within browser sessions, including data movement, task execution, and decision-making. This shifts security concerns from simple access control to governance of intent, behavior, and downstream actions, increasing the need for continuous, contextual enforcement within the browser itself.
3. What should security leaders evaluate beyond visibility in the browser?
Visibility alone is no longer sufficient. Leaders should assess whether their security architecture can:
- Enforce policy on autonomous and AI-assisted actions
- Govern data movement in real time
- Detect misuse originating from non-human actors (AI agents)
- Integrate cleanly with identity and Zero Trust frameworks
Without governance and enforcement, visibility risks becoming reactive rather than preventative.
4. Why are enterprises moving away from “rip-and-replace” browser strategies?
Most organizations already operate in multi-browser environments driven by user preference, application compatibility, and productivity requirements. Control-layer approaches that secure existing browsers align better with how work is done today and reduce user friction, shadow IT, and operational resistance.
5. How should leadership measure success in browser security initiatives?
Success should be measured by:
- Reduction in real security incidents tied to browser activity
- Minimal impact on user experience and performance
- Improved control over AI-driven workflows
- Seamless alignment with identity, access, and Zero Trust strategies
Ultimately, browser security should function as an invisible control plane—effective without being disruptive.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at info@intentamplify.com








