Imagine this: you finish a hectic day of meetings, shut your laptop, and without your intervention, your business systems automatically secure themselves at night. No mad rush of last-minute checklists, no searching for the “log out of all devices” button. That’s the magic of modern Identity and Access Management (IAM) tools.
In 2025, IAM is no longer just a behind-the-scenes IT function. It has evolved into the silent gatekeeper of enterprise trust, seamlessly balancing convenience and security in a world where hybrid work, AI-powered processes, and machine identities are the new norm. In this article, we’ll explore the most capable IAM solutions available this year, their real-world applications, and how to choose the one that fits your organization like a glove.
What IAM Means in 2025
Identity and Access Management is the policy, technology, and process framework that guarantees the right individuals, increasingly the right AI agents, have the right access at the right time.
Initially viewed as merely “password management,” IAM today is heavily embedded in enterprise strategy. It encompasses:
- Authentication and authorization for employees, contractors, and systems.
- Access governance and lifecycle management.
- Protection of privileged credentials.
- AI-driven threat detection to identify suspect access behavior in real time.
As per Gartner, identity security is now at the very base of contemporary cybersecurity policies. And with the quick embrace of generative AI, the term “identity” has grown to embrace not just human users, but also bots, APIs, and automated tasks.
Top IAM Tools to Watch This Year
A number of IAM platforms are making the benchmark for enterprise-class identity security in 2025.
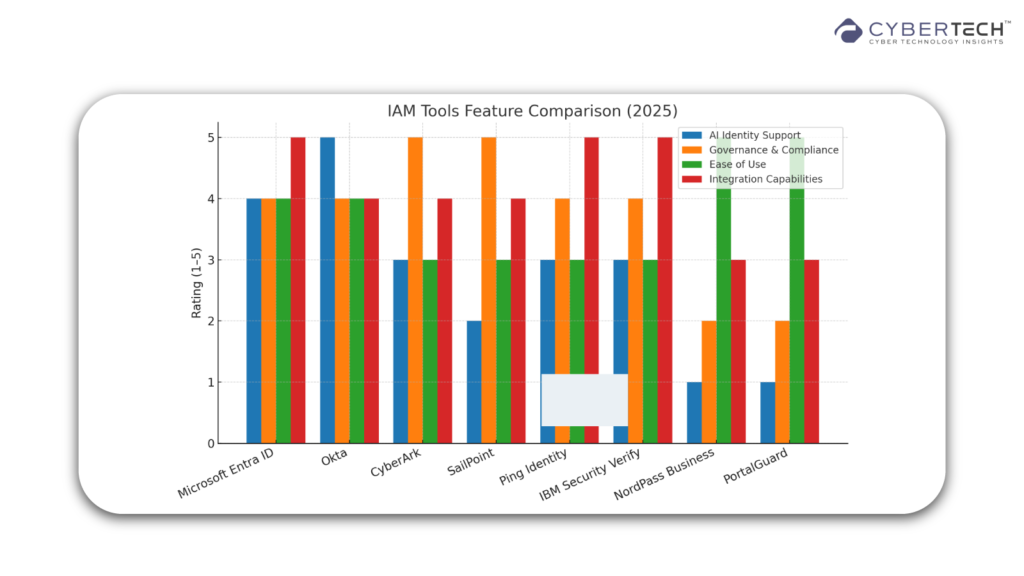
Microsoft Entra ID remains an easy choice for organizations that are already committed to Microsoft’s ecosystem, featuring rich integration, rich multi-factor authentication, and conditional access policies that respond to user risk profiles.
Okta has made a strong move ahead with its “Auth for GenAI” capability, created to protect non-human identities like AI assistants and bots. This represents a significant change – businesses aren’t simply safeguarding human logins anymore; they’re guarding the identities of AI entities engaging with sensitive information.
CyberArk, which Palo Alto Networks recently spent close to $25 billion to acquire, offers unparalleled PAM capabilities that are essential for protecting administrative and system-level accounts that can open up entire networks.
SailPoint tends to be popular for its governance features, offering end-to-end visibility into what people have access to, and whether that access is still current.
Ping Identity and IBM Security Verify stand out with flexibility, scalability, and robust support for hybrid environments, crossing on-premises and cloud-based systems.
Organizations that want simplicity without compromising on protection have access control and password management user-friendliness from NordPass Business and PortalGuard, suitable for small and mid-sized businesses that still require enterprise-level protection.
Why This Matters More Than Ever
One CISO I recently interviewed likened good IAM to a well-trained flight attendant,” always there when you need it, hardly seen when you don’t.” That’s the spirit of good IAM: it humbly works in the background, ensuring all identities, whether human or machine, engage with your systems in a controlled, compliant, and secure manner.
This is particularly critical today, when the typical business is balancing thousands of active user identities, dozens of cloud platforms, and several AI integrations, all having highly specific access controls.
Selecting the Proper IAM Solution in 2025
Evaluating IAM solutions this year, consider the following dimensions to focus on:
Identity Coverage Breadth – Does the solution protect solely human identities, or will it also deal with AI agents, service accounts, and third-party integrations? Okta has already adjusted to this increased identity scope.
Governance versus Everyday Access – SailPoint is best at governance and compliance audits, whereas daily sign-in ease would perhaps be served by NordPass or PortalGuard.
Ecosystem Interoperability – If your company is deeply committed to Microsoft, Entra ID has native interoperability. For hybrid or multi-cloud environments, Ping Identity and IBM IAM provide nimble deployment options.
Future-Proofing – Check for signs of innovation, including AI-driven anomaly detection, adaptive auth, or support for security orchestration platforms. Palo Alto Networks’ acquisition of CyberArk indicates a convergence toward security ecosystems.
Usability – Even the most secure IAM is worthless if employees work around it. Prioritize platforms that combine strong protection with low friction in the user experience.
The Bottom Line
In 2025, IAM is no longer only about blocking the bad guys; it’s about giving your business the ability to move faster, with trust, in a digital world where identities are exploding. Your solution will integrate seamlessly into your processes, respond to changing security requirements, and shield your people and your AI-powered systems from harm without hindrance.
When selecting, keep in mind: your IAM solution isn’t software; it’s a growth and security partner for your business.
FAQs
1. Why is IAM so vital in 2025?
IAM is the new frontline against emerging digital risks, particularly with the growth of AI and non-human identities touching enterprise environments.
2. Which IAM solutions manage identity through AI most effectively?
Okta’s “Auth for GenAI” is among the first to tackle AI agent authentication and access control explicitly.
3. Why is the CyberArk–Palo Alto Networks acquisition noteworthy?
The acquisition brings privileged access management into Palo Alto’s wider security platform, allowing seamless defense across identity and network layers.
4. Do IAM tools exist only for large companies?
No solutions like NordPass Business and PortalGuard are made for small and mid-sized businesses, but still offer enterprise-class security.
5. How can I determine that my IAM tool is future-proof?
Look for features such as AI-based risk scoring, adaptive authentication, wide integration capability, and module-based scalability to adapt to evolving business requirements.
For deeper insights on agentic AI governance, identity controls, and real‑world breach data, visit Cyber Tech Insights.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at sudipto@intentamplify.com.








