In this connected age, cyber espionage has proven to be one of the most subtle and debilitating threats to global businesses. This type of cybercrime differs from the usual financially driven and swiftly executed ones, as it involves stealth, persistence, and information gathering. Nation-states and highly capable groups target corporations for sensitive information, trade secrets, and strategic advantage over the long term. For cross-border enterprises, this war without a visible front has turned into an emblematic risk in 2025.
What Is Cyber Espionage and Why Does It Matter?
Cyber espionage is the process of penetration into networks and systems for stealing sensitive information undetected. The data stolen tends to comprise intellectual property, business plans, classified research, or government intelligence. As opposed to brute-force attacks or ransomware, espionage-based campaigns focus on stealth. Attackers spend months internalizing themselves in a network before making a move.
What makes this threat particularly perilous is its purpose. Rather than a direct financial reward, it seeks to gain long-term competitive or political leverage. For governments, this could be to tap into defense plans. For companies, there can also be theft of trade secrets that depreciates years of research and development.
A prime example is 2020, the SolarWinds attack. It was the most sophisticated supply chain breach. This one enabled state-sponsored threat actors to exfiltrate sensitive information from U.S. federal agencies and private companies. The attack demonstrated that espionage is not disruptive. Silently exfiltrating valuable intelligence predicated the espionage.
The expense is astronomical. In IBM’s Cost of a Data Breach Report 2024, state attacks, often associated with espionage, run $4.91 million per incident, much higher than the average cyberattack. For international businesses, this is not an IT issue but one for the boardroom.
Techniques and Tactics of Cyber Espionage
Spear-Phishing and Social Engineering
Phishing is usually the initial step in an espionage campaign, but these attacks are not at all random. Phishers who intend specifically for espionage target individuals and often impersonate government agencies, executive leadership, or a trusted supplier. For example, APT29 (“Cozy Bear”) used spear-phishing emails claiming to be COVID-19 vaccine updates to gain access to pharmaceutical research networks. This illustrates how the bad guys use existing crises to create trust and a sense of urgency.
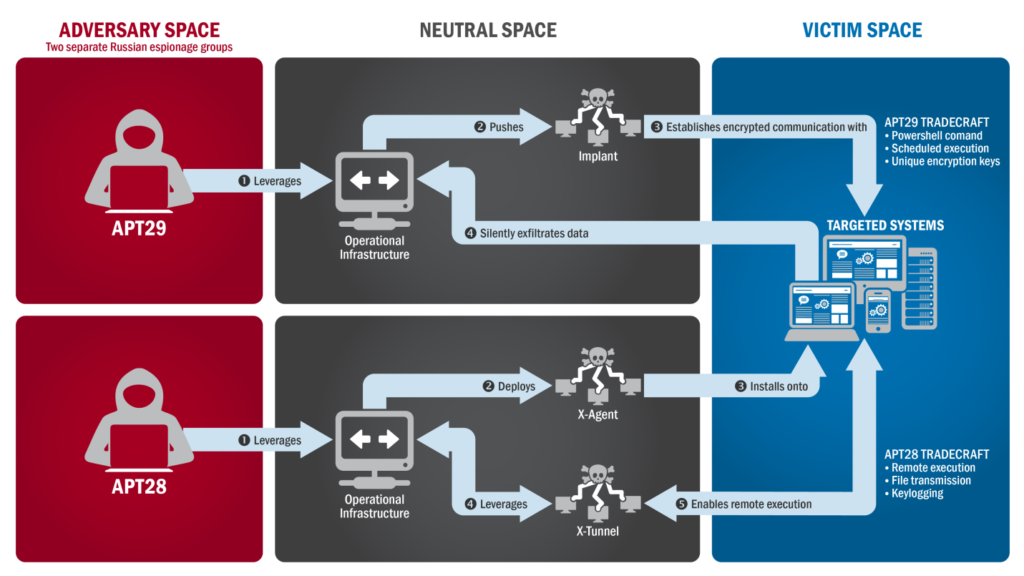
Supply-Chain Compromises
The most dangerous method we have learned about in recent years is the attack against trusted third parties. The SolarWinds exploit in 2020 demonstrates this behavior. Attackers plant malware either in the malware identification/monitoring software or the victim’s software, indicating successful exploitation in conjunction with the legitimate software updates to thousands of organizations simultaneously. Since organizations typically trust vendor updates by default, the attackers had an easy path to observe federal agencies, banks, and Fortune 500 corporations. Supply chain sabotage sidesteps the best front lines and compromises the heart of digital trust in the process.
Exploiting Zero-Day Vulnerabilities
Nation-state spy teams frequently leverage zero-day exploits. Attackers exploit known vulnerabilities to vendors in zero-day attacks, but the security community remains unaware of them. This sort of attack is most advantageous for the attackers since defenders will be unaware, with no previous knowledge or patches. For example, in 2021, Chinese-aligned teams used a developed zero-day exploit for Microsoft Exchange servers and then entered into the platform and were able to exploit it was able to achieving a global breach by compromising any sensitive corporate communications. Zero-day exploits typically represent sophisticated levels of spy teams due to above-average resources, sophistication, and intent over a length of time.
Cargo Cult Patterns of Attack Using Malware
By contrast, ransomware or denial-of-service attacks are forms of cyber espionage. These are inherently stealthy. Cyberattackers prefer to plant substantial malware implants that can survive months or years before they detect them. The attackers steal this information in small, often difficult-to-observe, fragments.
This tenacity is what makes espionage unique. As per Mandiant’s 2023 report, cyber espionage actors tend to linger within a victim network for more than 200 days before they are discovered. Actors may already possess terabytes of sensitive information by the time they discover an intrusion.
The Impact on Enterprises and How to Defend
For businesses, the harm goes far beyond monetary damages. Stolen intellectual property can eliminate competitive advantage, and unauthorized access to private information about customers or business partners can destroy trust as well. In industries such as aerospace and energy, and technology, espionage has already seen billions in losses relating to stolen innovations and patents.
Take the repeated claims of Chinese cyber espionage on U.S. tech companies, wherein they supposedly exfiltrated their billions-dollar trade secrets over the years. Not only does it incur immediate economic damage, but it also has long-term setbacks to staying on top in the market.
In order to counter such threats, businesses need to do the following in terms of adopting a multi-layered and intelligence-based defense:
- Threat intelligence initiatives that give them visibility into the latest espionage groups and techniques.
- XDR solutions that correlate threats from across endpoints, servers, and cloud environments.
- Zero Trust Architecture that guarantees that no user or system will be automatically trusted, even when they are located inside the corporate perimeter.
- Supply chain risk management in which third-party vendors and partners are watched with the same intensity as internal systems.
In the end, it all comes down to resilience against cyber espionage. A business can’t think it is too small or too insignificant to take its chances. In the geopolitics of today, any organization has the potential to be an intelligence source.
Conclusion
Cyber espionage has become one of the biggest threats to global businesses. Unlike speedy ransomware attacks, espionage is patient and tenacious. The attackers are not amateur thieves but well-funded organizations with long-term objectives. To businesses, dismissing this threat is jeopardizing innovation, reputation, and national security. In 2025, it is no longer a choice to treat it as a government concern alone. It is a board-level priority for each organization.
FAQs
1. Can you briefly describe in layman’s terms what cyber espionage is?
It is the secret action of hackers stealing classified information from either a government or an organization for long-term strategic use.
2. Who is usually targeted with cyber espionage?
Government agencies, defense contractors, technology companies, energy companies, and multinational corporations are the usual targets where a high number of attacks occur.
3. In what way is it different than cybercrime?
Cybercriminals typically act in a money-driven and instantaneous manner, while spies continuously hone their practices to collect intelligence over time.
4. What are common indicators of cyber espionage on a network?
Unusual data exfiltration, open backdoors, unauthorized access attempts, and unregulated activity over long periods.
5. How do organizations protect against it?
By utilizing threat intelligence, understanding zero trust, managing supply chains, and maintaining next-gen detection and response tools.








