Few challenges persist as stubbornly, and as silently, as the legacy technology embedded in Europe’s operational environments. While digital transformation headlines dominate strategy decks, the reality beneath factory floors and energy grids often tells a more precarious story. Systems designed for reliability decades ago are now forced to face threat landscapes they were never built to withstand. The latest research commissioned by TXOne Networks brings new clarity to this quiet crisis.
This Report, conducted in March 2025 across six European markets, the study reveals that nearly half of the surveyed organisations still operate with at least 50% of their OT (Operational Technology) environments running on legacy platforms, many dating back to Windows XP, 7, or even older proprietary controls.
An Operational Backbone with Hidden Risk
Operational technology is the beating heart of modern industry, powering sectors from manufacturing and utilities to pharmaceuticals and transportation. Its resilience is mission-critical. Yet the same systems that ensure consistent production often lack the basic security controls now standard in IT environments.
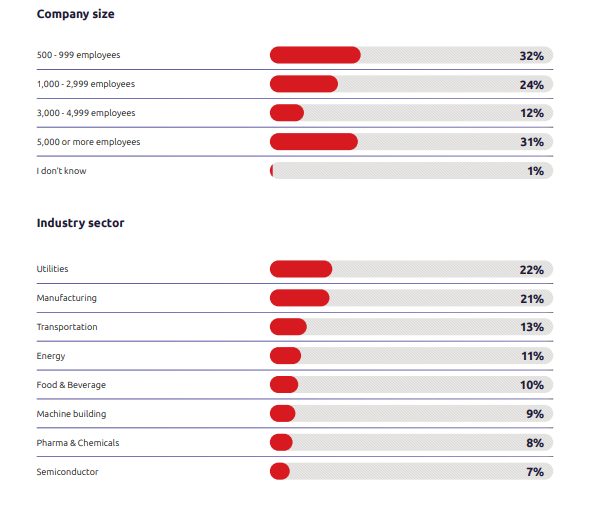
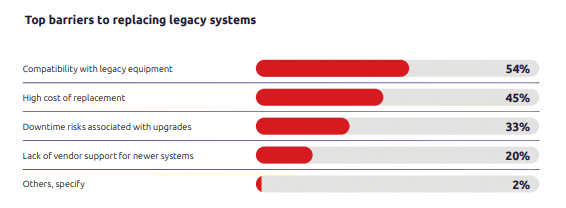
As highlighted in the TXOne report, more than 20% of organisations admit that three-quarters or more of their OT environment is legacy-based. The persistence of these ageing systems is not simply inertia; it’s rooted in two very practical barriers. Compatibility constraints (54%) and high replacement costs (45%). When a single machine downtime can halt production for days, leaders rightly weigh upgrade decisions carefully. Unfortunately, this caution has allowed threat actors a window of opportunity.
An Expanding Attack Surface
One of the more sobering findings comes from the TXOne report’s incident statistics. 43% of European industrial firms confirmed they had experienced a cyberattack specifically targeting their legacy OT systems in the last year alone. This rate spikes dramatically in certain geographies: Poland (60%) and the UK (59%) top the chart.
The nature of these threats is no longer theoretical. Certainly, Malware and virus infections remain the leading concern (52% of respondents), followed by unauthorised access (36%) and ransomware intrusions (32%). For industrial sectors like energy, semiconductor manufacturing, and machine building, these risks directly translate to disrupted supply chains, potential safety hazards, and significant financial liabilities.
Barriers to Change: Cost, Complexity, and Continuity
Why, then, are more firms not racing to overhaul these environments or at least shield them with dedicated protections? The answer is complex, but unsurprising to any OT security leader. 44% worry that new security tools will degrade system performance, while 42% cite conflicts with critical OT applications as a primary concern.
Additionally, a skills gap persists. Thirteen percent of organisations report insufficient in-house expertise to configure and maintain modern security controls within legacy-heavy OT environments. In interviews with European plant managers and OT directors, a recurring theme emerges; “Security is important, but not at the expense of production uptime.”

The Economic Equation: Upgrade vs. Protect
One might assume that if upgrades are so disruptive, protection must be the pragmatic alternative. Yet misconceptions cloud this path, too. 59% of respondents believe that deploying robust security is just as costly or only slightly less so than performing a complete upgrade. In reality, modern OT-native security solutions are engineered precisely to bridge this cost-performance gap.
62% of organisations now plan to adopt legacy-capable security solutions within the next cycle, with integration ease and zero operational disruption topping their must-have list. This shift signals that boards and security teams are finally converging on a shared goal: safeguarding productivity without compromise.
A Pragmatic Path Forward
In the evolving landscape of industrial cybersecurity, protecting legacy OT assets demands a measured, strategic approach, not knee-jerk replacements nor superficial fixes. Over the years of consulting with CISOs and OT directors, three guiding principles have consistently delivered results across sectors and geographies.
1. Accept Legacy as a Strategic Constant
Complete eradication of legacy OT is an admirable vision, but rarely a realistic goal. From power grids to chemical processing plants, critical assets designed decades ago often continue to deliver value with minimal downtime. Leaders must plan for a hybrid state where old and new coexist for years, perhaps decades, to come.
This mindset shift is crucial: once boards acknowledge that legacy is not merely a technical debt but a strategic constant, cybersecurity planning becomes proactive rather than reactive. This includes setting clear timelines for phased upgrades, while also investing immediately in solutions tailored to secure what cannot be replaced overnight.
2. Deploy Non-Disruptive & Adaptable Security
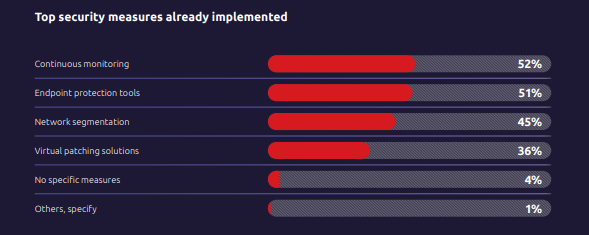
When the TXOne report shows that 44% of leaders fear system performance degradation, it signals a truth every security practitioner knows: controls must be as invisible as they are effective. Continuous monitoring, lightweight endpoint protection, and virtual patching are three defensive pillars that align with this reality.
Modern OT-native solutions can segment networks, detect anomalies, and apply virtual patches without forcing a costly rip-and-replace of core equipment. For example, a semiconductor fabrication plant can deploy intrusion detection agents specifically designed for its legacy Windows XP controller, ensuring threat visibility without introducing downtime. Security tools must respect operational continuity as a non-negotiable, not an afterthought.
3. Build a Cross-Functional Security Culture
Technical controls alone cannot secure legacy environments. Silos between IT, OT, and compliance teams often stall even the most robust protection strategies. Eventually, Effective legacy OT security requires a cross-functional culture where engineers, plant managers, and CISOs jointly assess risks and design controls. This includes defining shared protocols for system updates, incident response, and continuous audit of vulnerable endpoints.
Additionally, upskilling frontline engineers with basic cybersecurity know-how fosters a first line of defense, turning operators into vigilant allies rather than accidental insiders.
4. Integrate Risk Governance with Business Continuity Planning
An expanded legacy OT security strategy must tie directly into enterprise risk governance frameworks. This means that exposure from unpatched legacy assets should be quantified and presented in the same board-level risk reports as financial, legal, or reputational risks.
For highly regulated sectors, such as pharmaceuticals and energy, this alignment is not optional. European regulators are steadily tightening compliance standards for critical infrastructure security. Firms that embed legacy system risk into their business continuity and compliance posture position themselves to meet both customer expectations and regulatory scrutiny.
5. Continuously Benchmark, Audit, and Adapt
Finally, securing legacy environments is not a one-off project; it is an ongoing commitment. The TXOne report makes it clear that threat actors are innovating just as fast as defenders. Industrial organisations must regularly benchmark their security measures, audit legacy systems for new vulnerabilities, and adapt controls accordingly.
Organisations that treat legacy OT as a living, evolving part of their attack surface, rather than static background infrastructure, are better equipped to maintain operational resilience amid escalating cyber threats.
TXOne Networks: A Note on Purpose-Built Protection
TXOne Networks, whose work serves as the foundation of this analysis, is one of the handful of vendors designing OT-native security expressly for the needs of legacy-heavy infrastructures. Solutions like Stellar Endpoint Security are engineered to secure assets dating back to Windows 2000 with virtually no effect on operational continuity. No single vendor can magic away the legacy problem overnight, of course, but such purpose-built solutions present security and operations teams with a credible middle ground.
Securing the Past to Secure the Future
Europe’s industrial core will increasingly depend on architectures designed when today’s threat profile was not yet imagined. As criminals become more skilled, the price of inertia becomes higher. Visionary leaders must weigh upgrade roadmaps against realistic protection approaches that secure legacy environments today.
For decision-makers who have this tricky balancing act assigned to them, the TXOne report offers evidence-informed benchmarking for boardroom debate, investment strategy, and regulatory preparedness.
FAQs:
1. Why don’t businesses simply replace aging OT systems?
Legacy OT replacement is costly and hazardous. Machines are often on production lines, and replacing them equates to extended downtime, lost sales, and complicated compatibility tests. Firms mostly opt for gradual upgrades along with extra security layers.
2. What makes legacy OT so easy to hack?
Older OT systems weren’t built with cybersecurity in mind. They often lack passwords, encryption, or modern updates. Hackers exploit these gaps because fixing them isn’t as simple as patching a laptop.
3. How can firms protect legacy OT without stopping production?
They can employ OT-designed security tools, such as network segmentation, virtual patching, and real-time monitoring, which quietly operate in the background. These block threats without disrupting business-as-usual.
4. Is it cheaper to add security than to replace everything?
Yes. Most people believe today’s OT security costs as much as complete replacement, but that’s a myth. Purpose-built solutions are cheaper, deploy faster, and steer clear of costly downtime.
5. What’s the initial step to lock down legacy OT?
Begin by determining which legacy systems are most vulnerable. Next, layer protection tools that do not disrupt production, educate employees on fundamental security, and make OT threats part of your core risk and continuity plans.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at sudipto@intentamplify.com.








