In the past few years, adoption of JSON Web Tokens (JWT) has expanded across cloud-native architectures, API-driven services, and federated authentication systems. Its promise is simple: a compact, interoperable means of asserting identity and authorization without the need for centralized session stores.
However, that simplicity masks a subtle, expansive attack surface that many senior leaders still underestimate. JWT mechanisms don’t offer security by default; they demand implementation discipline. And when that discipline lapses, the consequences can scale from unauthorized access to system-wide breach.
Public CVEs, recent expert analyses, and ongoing red-team findings show we’re still grappling with the same basic failures that have haunted JWT implementations for years. These failures aren’t academic. They’ve been observed in real products and can compromise critical business APIs and cloud services.
This article situates common JWT vulnerabilities in the strategic context senior decision-makers need to understand risk, prioritize remediation, and align technology controls with organisational risk.
The Architecture of Risk in JWT Systems
At its core, a JWT consists of three components: a header indicating algorithm metadata, a payload with claims, and a cryptographic signature. That structure inherently trusts the issuer’s signature.
If any part of that trust model breaks down, so do the security guarantees of the token. Yet many cloud and API environments inadvertently weaken this model at just the wrong places.
According to the OWASP testing guide, one of the most serious JWT weaknesses is simple: failure to verify signatures before trusting token content. Attackers can alter the payload and still be accepted if signature checks are omitted or misconfigured.
Cloud deployments compound this risk. APIs often sit behind load balancers, microservices, API gateways, and serverless functions, each parsing tokens independently. A misconfiguration in even one service can bypass global identity policies. Without unified verification logic and consistent enforcement, attackers can tunnel forged or manipulated tokens into sensitive workflows.
Algorithm Confusion and Header Manipulation
One of the most pernicious classes of JWT bugs stems from “algorithm confusion.” In theory, the JWT header merely declares what algorithm was used to sign the token. In practice, some libraries historically trusted that header and verified the token using a symmetric key, even if the issuer intended asymmetric signing.
Analysts have described how this flaw enables attackers to switch from RS256 (asymmetric) to HS256 (symmetric) and sign tokens with a known public key, thereby forging valid credentials.
Multiple vulnerabilities dating from 2023 through late 2025 hinge on algorithm decision points that libraries expose to malicious manipulation. In one notable NIST-tracked CVE, a popular JWT JavaScript library accepted algorithm definitions from untrusted token headers, leading to “algorithm confusion” that could be exploited in production.
Unsigned Tokens and the “None” Algorithm
Yet another variation on this theme is the so-called “none” algorithm attack. Some implementations continue to support an unsigned token mode intended for testing or non-sensitive use cases.
If production code accidentally allows tokens with “alg”: “none”, attackers can strip the signature entirely and still be admitted. Even experienced implementers have fallen for this.
This kind of flaw is easy to overlook when teams treat token issuance and validation libraries as “plug-and-play.” The JWT spec’s flexibility becomes its vulnerability when teams fail to explicitly whitelist acceptable algorithms at runtime, or when default library behavior isn’t aligned with security policy.
Secret Management: The Achilles’ Heel of Symmetric Tokens
JWTs using symmetric signing (e.g., HS256) rely on shared secrets that must stay confidential. Weak keys, whether short, predictable, or hard-coded, are easy to brute-force. Weak secrets, whether due to lazy generation or careless storage, have cost organisations dearly because once an attacker derives the secret, they can create valid tokens at will.
API environments exacerbate this risk because distributed services often require copies of secrets in multiple runtime environments. Leaked secrets can live for months before discovery, allowing unfettered API access or privilege escalation in cloud accounts.
Replay Attacks and Stale Claims
JWTs are often chosen for scalability because they’re stateless: servers don’t hold session state. But this same design means tokens can’t easily be revoked. If a JWT with a long lifetime is intercepted, attackers can replay it until expiry. Worse, tokens that carry authorization claims (like role or permission scopes) can become stale if the underlying identity changes and the system never reissues new tokens.
Replay and stale token issues matter intensely in cloud contexts where ephemeral credentials and autoscaling services create a high ratio of token exchanges. Without a robust revocation or session invalidation strategy, attackers can exploit what architects once called “graceful scalability” into a silent leveraged breach.
Injection Vectors and Kid Manipulation
Attackers don’t only modify algorithms or payloads. JWT headers can contain parameters like kid, a key identifier that tells the server which key to use for validation. If an implementation doesn’t validate the kid, attackers can inject controlled values that redirect the server to use attacker-controlled public keys, potentially signing arbitrary tokens that the system trusts.
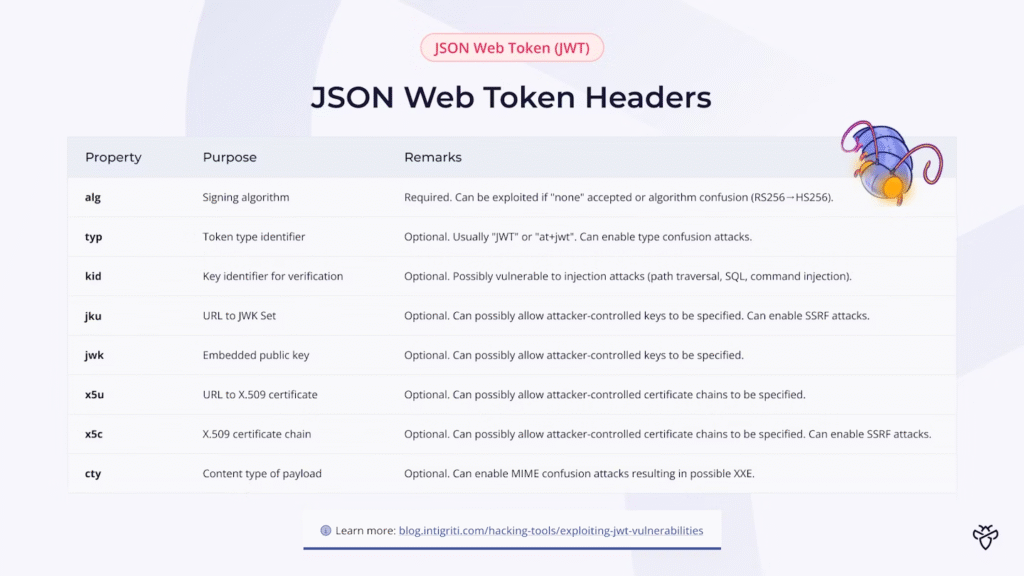
This pattern of injection shows how seemingly benign features can become powerful weapons when validation logic isn’t exhaustive, and boundary checks are lax, classic software defects with catastrophic identity implications.
Strategic Implications for Decision-Makers
For executives weighing identity strategies, these vulnerabilities translate into three hard considerations:
- Security is not automatic. Just choosing JWTs doesn’t harden authentication. Without disciplined implementation, the token becomes a lever for attackers rather than a defense.
- Library and dependency hygiene matters. Recent CVEs across JWT libraries in Node, Java, and other ecosystems demonstrate that token security isn’t static. Organisations need active monitoring and upgrade policies.
- Token governance must scale with your API footprint. Cloud and microservices environments demand coordinated key management, algorithm policies, and centralized verification logic rather than ad hoc checks in scattered services.
Risk posture must explicitly account for the fact that a single misconfiguration in a JWT parsing path can undermine an entire API armoury.
Rebuilding Trust at the Token Layer
JWT security failures rarely come from the protocol itself. They come from misplaced trust and unchecked assumptions in implementation.
For stakeholders concerned about cloud API risk, treat JWTs not as a solved problem, but as another control in your identity and access management risk portfolio.
Addressing these vulnerabilities requires explicit algorithm whitelisting, robust secret management, short token lifespans with revocation or rotation, and consistent signature validation across all services.
Ignoring any of these elements invites attackers into the very systems meant to verify and secure digital identities.
FAQs
1. Are JWTs still safe for enterprise cloud and API authentication?
Yes, but only if treated as a security control that requires active governance. JWTs fail when teams assume defaults are safe. Misconfigured validation, weak keys, or inconsistent enforcement across services can quietly negate the entire trust model.
2. What is the most common JWT mistake that leads to breaches?
Skipping or inconsistently enforcing signature verification. One microservice that accepts a token without strict checks can become the attacker’s side door, even if every other system is hardened.
3. Should enterprises avoid symmetric signing (HS256) in distributed environments?
Shared secrets spread across containers, pipelines, and regions tend to leak or linger. Asymmetric keys reduce blast radius, though they add operational overhead. It’s a trade-off between simplicity and containment.
4. How do you reduce JWT replay and stale-claim risk in cloud-native systems?
Short lifetimes. Frequent rotation. Central revocation or session introspection for high-risk actions. Stateless sounds efficient until you need to kill access fast. At scale, pure statelessness becomes a liability.
5. Where should leaders focus investment first to lower JWT-related risk?
Centralized validation and key management. One enforcement layer at the gateway or identity tier beats dozens of ad hoc checks inside services. It’s less elegant architecturally, but far safer operationally. Consistency wins over purity.
To participate in upcoming interviews, please reach out to our CyberTech Media Room at info@intentamplify.com



